 [Max Weisel] recently created a Peltier-based cooling/heating system that fits into a backpack. The system uses two Peltier units, each running at 91.2 watts, with computer heat sinks mounted on one side of the unit to dissipate the excessive amounts of heat generated. While he was originally trying to build a cooling backpack, the use of the Peltier units meant that the cool side would become warm when the direction of current was switched, meaning that the backpack could become a heating backpack with the flip of a switch. In order to power the two Peltier units, he uses two 12v motorcycle batteries, weighing in at around 5 pounds each. While this backpack might be a little heavy for your back, it looks promising for anyone who needs to keep things cool (or warm) on the go.
[Max Weisel] recently created a Peltier-based cooling/heating system that fits into a backpack. The system uses two Peltier units, each running at 91.2 watts, with computer heat sinks mounted on one side of the unit to dissipate the excessive amounts of heat generated. While he was originally trying to build a cooling backpack, the use of the Peltier units meant that the cool side would become warm when the direction of current was switched, meaning that the backpack could become a heating backpack with the flip of a switch. In order to power the two Peltier units, he uses two 12v motorcycle batteries, weighing in at around 5 pounds each. While this backpack might be a little heavy for your back, it looks promising for anyone who needs to keep things cool (or warm) on the go.
Author: Nick Caiello36 Articles
Palin Email Hack Post Mortem

A few days ago a lone individual decided to crack [Governor Sarah Palin]’s private Yahoo! email account. He did this by navigating the password reset procedure. [Gov. Palin]’s birthday was publicly available and Wasilla only had two zip codes to guess. The follow up question “Where did you meet your spouse” required some more research. They met in high school so a few more guesses turned up “Wasilla high” as the answer. The original poster then read every single email only to discover that there really wasn’t anything of interest there. Frustrated, he posted the details to 4chan to let any wonk have at it. /b/ members began posting screenshots of the account, but very little came of it.
One screenshot of her inbox even revealed her daughter Bristol’s cell phone number. While there was no groundbreaking political information revealed, it is important to point out that it appears that Gov. Palin was using this private account to correspond to her assistants about potentially sensitive government information. This security breach should serve as a wake-up call to many public officials by showing how dangerous it can be to have a private e-mail account, especially when a free web-based service such as Yahoo! is used.
Toaster Computer

[Gordon Johnson] recently completed part 1 of his toaster computer project. He used a standard four slot toaster as the enclosure and cut holes for access to the ports and a wireless antenna. While the specifications of the components used are not mentioned, the build is well documented on his site, complete with lots of pictures and a video. While he used a traditional fan based cooling method for part 1 of the build, he plans on using a special cooling method for part 2 that uses aluminum and mineral oil to create a thermoelectric cooling effect.
Security Flaw Allows Full Access To Locked IPhones
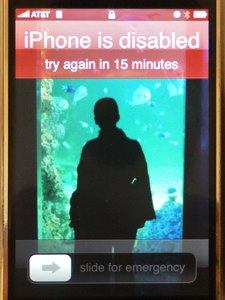
[greenmymac] on the MacRumors forums recently exposed a security flaw that allows anyone full access to a locked iPhone running firmware version 2.0.2. The flaw works by entering the emergency call menu of a locked iPhone, and double tapping the home button. This opens the iPhone’s Favorites menu, allowing anyone in your Favorites to be called. From here, an attacker has access to your SMS messages and potentially your email or Safari browser. While we are sure that Apple has a patch for this flaw on the way in the next firmware update, there is a temporary way to secure your locked iPhone. Simply enter the Settings menu on your iPhone and enter General > Home Button and select “Home” or “iPod”. Now when you double tap your home button, it will navigate to either your home screen or the iPod screen. While this fix might be annoying for some, as of right now it seems like the only way to secure your locked iPhone.
[photo: Refracted Moments™]
[via Gizmodo]
Parents Beware Of “digital Drugs”

In what some might call a sensationalist article, USA Today reporter [Kim Komando] warns parents of a new danger to their kids: digital drugs. Throughout the article, [Kim] tries to explain how binaural beats (idosers) can effect the brain in many different ways, claiming that some even emulate the effects of illegal drugs. Furthermore, she claims that the “digital drugs” can act as a gateway to trying real drugs. While it seems unapparent to [Kim] that I-Doser has been around for years, it’s not surprising that this article is only being published now. While I understand her argument, parts of it just seem illogical. If anything, wouldn’t binaural sounds provide kids an alternative to illegal drugs? If these sounds really provide the same effects as drugs, wouldn’t they act as a safer option to kids? While this story seems to be one of many sensational stories warning parents to protect their kids, it seems as though parents should really be warned about these sensational stories that are concocted solely to sell newspapers.
[via Woot]
[photo: BrittneyBush]
Russia Vs Georgia, The Online Front

While we’re sure that just about everyone has heard about the conflict between Russia and Georgia, few have probably heard about the role of cyber attacks in the conflict. Shortly before Russia’s armed response, Georgian state web servers were attacked by individuals assumed to be Russian hackers. This attack almost completely obliterated Georgia’s online presence by shutting down the website for the Ministry of Defense, and the Central Government’s main site. The Russian attackers seem to be using some form of sustained DDoS to keep many Georgian sites offline. In an effort to preserve some web presence, the Georgian Government transferred [President Mikheil Saakashvili]’s site to a US hosting provider in Atlanta. The Ministry of Foreign Affairs even created a BlogSpot page after their website initially went down. While politically motivated DDoS attacks have not been rare in past months, this seems to be the first time where the attacking party can be clearly identified. This seems to be the start of a trend where the unconventional methods of cyber warfare are used to gain an advantage over the enemy.
[photo: somefool]
Homeland Security Issues Policy On Laptop Seizures

The US Department of Homeland Security recently disclosed a new policy that allows agents to seize laptops, or anything capable of storing information, “for a reasonable period of time”. Okay, so this seems normal; A government agency is declaring they may confiscate personal property. However, the strange part of this story is that under this policy, federal agents can confiscate these things without any suspicion of wrong doing or any reason what so ever. So what happens to your personal data after they seize your laptop? Apparently they share the data with federal agencies, and in some cases the private sector, as additional services such as file decryption or translation are needed. While this may seem like a major violation of privacy, it is important to note that this policy only applies to people entering the United States. However given the direction that our federal government is moving in the area of security, it wouldn’t surprise me if this policy will soon apply for domestic flights as well.
[photo: postmodern sleaze]
[via eff.org]










