The greatest computer Apple will ever make isn’t the Apple II, it isn’t the Bondi Blue iMac, it isn’t the trash can, and it certainly isn’t whatever overheating mess they’re pushing out now. The best computer Apple will ever make is the SE/30, at its time a server in a tiny portable shell, and capable of supporting 128 Megabytes of RAM thirty years ago.
Over the years, people have extended and expanded the SE/30 to absolutely ludicrous degrees, but now we have a simple way of adding WiFi to this classic computer. Over on the 68kmla forums, [ants] discovered a tiny cheap card that could easily serve as an Ethernet to WiFi bridge. After attaching this card to a Danaport Ethernet card and bending some aluminum for a bracket, they had a WiFi antenna sticking out of the back of a 30-year-old computer.
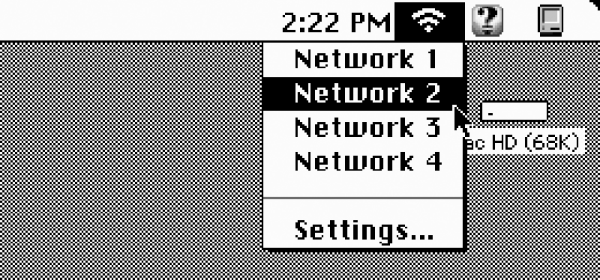
But adding a WiFi card to an old computer is nothing new — this could have been done with a Pi, or if you’re a hacker, a TP-Link router flashed with OpenWRT. To really do this right, you’ll need integration with the operating system, and that’s where this build goes off the rails. [ants] wrote a WiFi extension for System 7 (with the relevant GitHub)
The problem with the Vonets WiFi card is that configuration has to be done through a browser. Since there are no modern browsers for classic macs, this meant either pulling out a PowerBook or doing the configuration through your daily driver desktop PC. The WiFi extension gets around that by giving a classic mac the ability to configure the Vonets card almost automatically. This extension also looks like how you would configure the WiFi on a modern mac, complete with the WiFi icon in the toolbar. It’s beautiful, and one of the rare examples of modern 68k mac programming.
As for what you can do by adding WiFi to a 30-year-old computer with a 16MHz processor, the answer is a resounding, ‘not much’. Your choice of browsers is limited (iCab seems to be the best), but you can load the Google homepage slowly. HTTPS isn’t going to work, and the Internet right now is full of megabytes of Javascript cruft. If you find a nice, lightweight web page — such as the Hackaday Retro Edition, for example — you’re looking at a capable web browsing machine. Of course, the real use case for giving the SE/30 WiFi is file transfer around the home network, but still: it’s WiFi for the best computer Apple ever made.





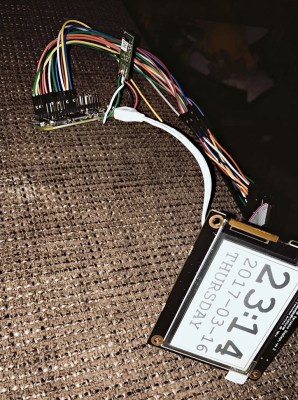 [Jannis Hermanns] couldn’t find a reason to control this outburst of nostalgia for the good old days of small, expensive computers and long hours spent clawing through the LEGO bin to find The Perfect Piece to finish a build. It turns out that the computer part of this replica was the easy part — it’s just an e-paper display driven by a Raspberry Pi Zero. Building the case was another matter, though.
[Jannis Hermanns] couldn’t find a reason to control this outburst of nostalgia for the good old days of small, expensive computers and long hours spent clawing through the LEGO bin to find The Perfect Piece to finish a build. It turns out that the computer part of this replica was the easy part — it’s just an e-paper display driven by a Raspberry Pi Zero. Building the case was another matter, though.











