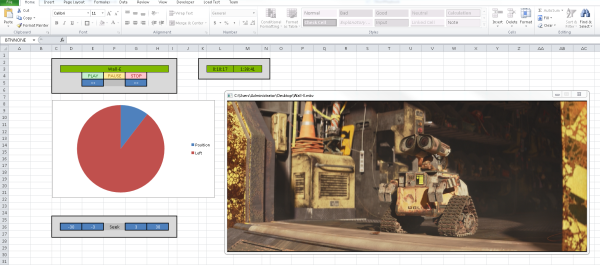
The Excel subreddit exploded earlier this week when redditor [AyrA_ch] shared his custom spreadsheet that allowed him to play video files on a locked-down work computer. How locked down? With no access to Windows Media Player and IE7 as the only browser (all plugins disabled, no HTML5), Excel became the unlikely hero to cure a 3-hour boredom stint.
Behind the cascade of rectangles and in the land of the Excel macro, [AyrA_ch] took advantage of the program’s VBA (Visual Basic for Applications) functions to circumvent the computer’s restrictions. Although VBA typically serves the more-complex-than-usual macro, it can also invoke some Windows API commands, one of which calls Windows Media Player. The Excel file includes a working playlist and some rudimentary controls: play, pause, stop, etc. as well as an inspired pie chart countdown timer.
As clever as this hack is, the best feature is much more subtle: tricking in-house big brother. [AyrA_ch]’s computer ran an application to monitor process usage, but any videos played through the spreadsheet were attributed to Excel, ensuring the process usage stayed on target. You can download it for yourself over on GitHub.