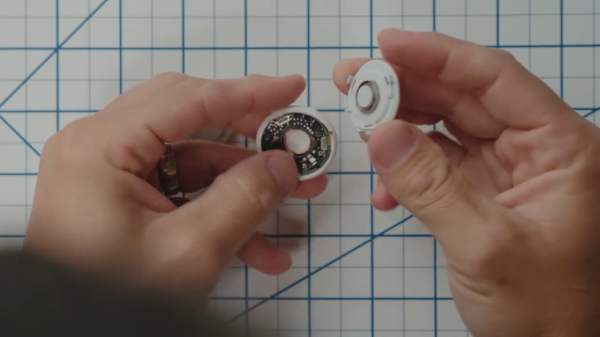
Occasionally, the extra features added to a product can negate some of the reasons you wanted to buy the thing in the first place. Take, for example, Apple’s AirTag — billed as an affordable way to link your physical stuff to your phone. If some light-fingered ne’er-do-well wanders by and half-inches your gear, you get notified. The thing is, the AirTag also has an anti-stalking measure, which after a while, notifies nearby iPhones, should the tag move but not be near your iPhone!
In a recent video, [David Manning] explains that this feature is great for preventing the device from being used to track people. But it also means that if said thief happens to own an iPhone, they will be notified of the nearby tag, and can find it and disable it. So in the end, it’s a bit less useful as an anti-theft measure!
The solution is to pop the back off the tag and yank out the little sounder module from the rear plastic. You lose the ability to locate the tag audibly, but you gain a little more chance of returning your stolen goods. Apple could easily remove this feature with a firmware update, but it’s a matter of picking your poison: antistalking or antitheft?