When we have two 3D printed parts that need to fit together, many of us rely on pins and holes to locate them and fix them together. [Slant 3D] has explored some alternative ideas in this area that may open up new avenues for your own designs.
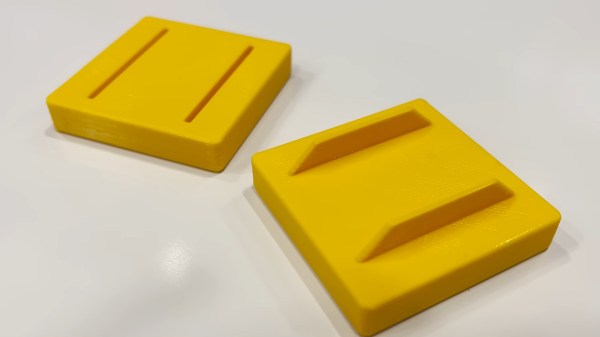
Their first idea was to simply chamfer the pins and holes. This allows the object to be printed in a different orientations without compromising the fit. It also makes the features less brittle and creates a broader surface for gluing. Another alternative is using fins and slots, which again add robustness compared to flimsy pins. By chamfering the edges of the fins, they can be printed vertically for good strength and easy location without the need for support material.
Neither option requires much extra fuss compared to typical pin-and-hole designs. Plus, both are far less likely to snap off and ruin your day. Be honest, we’ve all been there. Meanwhile, consider adding folded techniques to your repertoire, too.
Continue reading “Alternatives To Pins And Holes For 3D Printed Assemblies”