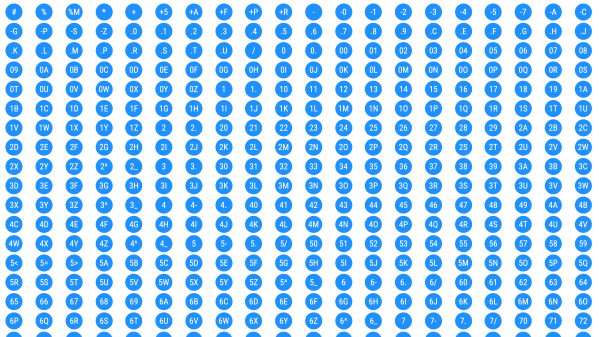
You’ve probably encountered this before — you have a circuit board that is poorly documented, and want to know the part number of a tiny SMD chip. Retro computer enthusiast [JohnK] recently tweeted about one such database that he recently found, entitled The Ultimate SMD Marking Codes Database. This data base is only a couple of years old judging from the Wayback Machine, but seems to be fairly exhaustive and can be found referenced in quite a few electronics forums.
Unlike their larger SMD siblings, these chips in question are so small that there is no room to print the entire part number on the device. Instead, the standard practice is for manufacturers use an abbreviated code of just a few characters. These codes are only unique to each part or package, and aren’t necessarily unique across an entire product line. And just because it is standard practice does not imply the marking codes themselves follow any standard whatsoever. This seemingly hodgepodge system works just fine for the development, procurement and manufacturing phases of a product’s lifecycle. It’s during the repair, refurbishment, or just hacking for fun phases where these codes can leave you scratching your head.
Several sites like the one [JohnK] found have been around for years, and adding yet another database to your toolbox is a good thing. But none of them will ever be exhaustive. There’s a good reason for that — maintaining such a database would be a herculean task. Just finding the part marking information for a known chip can be difficult. Some manufacturers put it clearly in the data sheet, and some refer you to other documentation which may or may not be readily available. And some manufacturers ask you to contact them for this information — presumably because it is dynamic changes from time to time. Continue reading “Decoding SMD Part Markings”