3D graphics were once the domain of university research groups and large, specialized computing systems. Eventually, they were tamed and became mainstream. Your phone, tablet, and home computer are all perfectly capable of generating moving 3D graphics. Incidentally, so is Microsoft Excel.
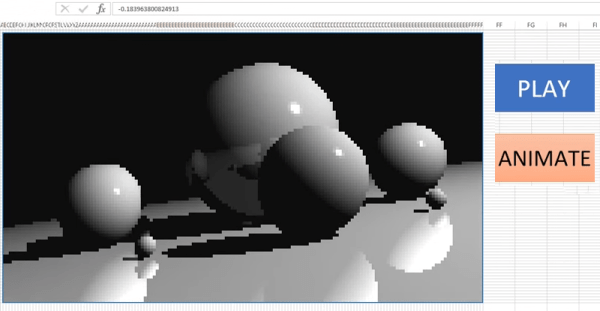
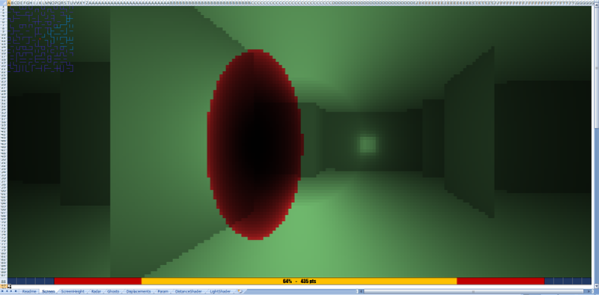
This is the work of of [s0lly], who has been experimenting wtih Excel in this way for quite some time. Starting with pseudo-3D graphics, the project then progressed to the development of a real 3D engine. Naturally, things couldn’t stop there. The next logical step was to advance to raytracing, which was pulled off with aplomb. Shiny spheres on featureless planes are par for the course here.
The graphics are necessarily basic, with resolutions on the order of 256×144. Output is by changing the individual color of the various cells of the spreadsheet. The relevant files are available on Github, for those eager to tinker with experiments of their own. We’ve seen others attempt similar work before, with [C Bel] writing a full game engine for the platform. Video after the break.