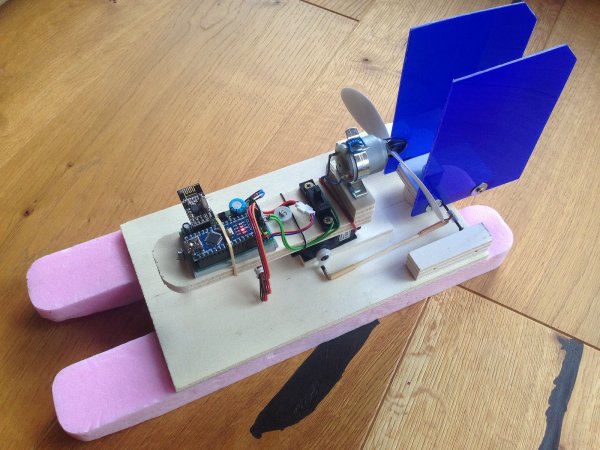
[Markus Gritsch] and his son had a fun Sunday putting together a little toy airboat from a kit. They fired it up and it occurred to [Markus] that it was pretty lame. It went forward and sometimes sideward when a stray current influenced its trajectory, but it had no will of its own.
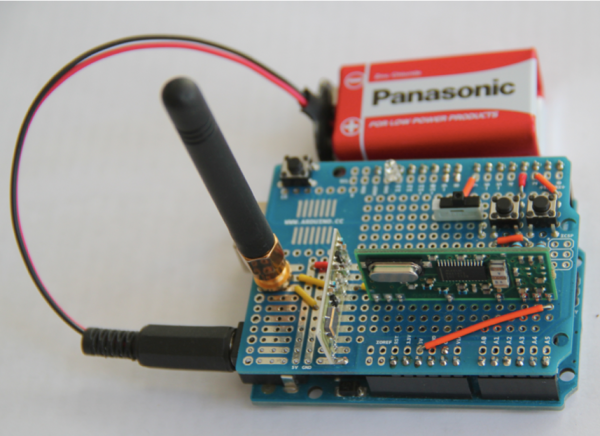
The boat was extracted from water before it could wander off and find itself lost forever. [Markus] did a mental inventory of his hacker bench and decided this was a quickly rectified design shortcoming. He applied a cheap knock-off arduino, equally cheap nRF24L01+ chip of dubious parentage, and their equivalent hobby servo to the problem.
Some quick coding later, assisted by prior work from other RC enthusiasts, the little boat was significantly upgraded. Now the boat could be brought back to shore using any R/C controller that supported the, “Bayang,” protocol. He wouldn’t have to face the future in which he’d have to explain to his son that the boat, like treacherous helium balloons, was just gone. Video after the break.
Continue reading “Cheap Toy Airboat Gets A Cheap R/C Upgrade”