If you ever mention to a normal person that you’re a hacker, and they might ask you if you can do something nefarious. The media has unfortunately changed the meaning of the word so that most people think hackers are lawless computer geniuses instead of us simple folk who are probably only breaking the laws meant to prevent you from repairing your own electronics. However, if you want a break, you can fully embrace the Hollywood hacker stereotype with Bitburner. Since it is all online, you don’t even have to dig out your hoodie.
The game takes place in 2077 where, apparently, people are still using green monochrome terminals and writing JavaScript code. Who knew? The operating system is suspiciously Linux-like with commands like alias, cat, cp, kill, and the like. We were nonplussed that in 2077 they’re still using vim, but you can use nano. We always thought real hackers would be emacs users. Our machine only starts out with 8 MB of RAM, too. Good thing you can virtually buy more.
We won’t quibble that cls is a synonym for clear or that you use help instead of man. It is, after all, a game. This means you don’t have to feel bad using the buy command to purchase a program on the virtual dark web, either. Hey, if you can shoot bad guys in an FPS game, why can’t you do business with fake cyber-criminals. Why should Grand Theft Auto players have all the fun?
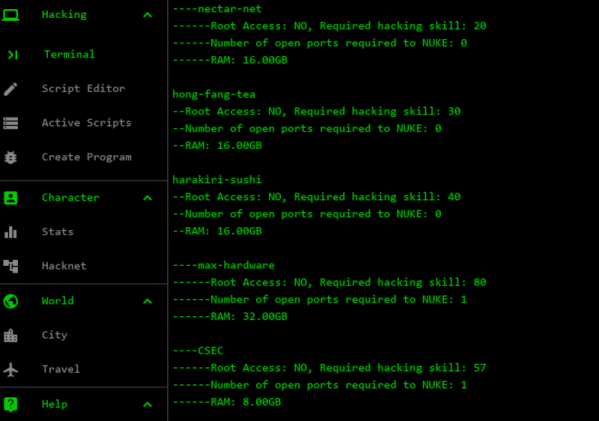
You know how in a video game you are a much better shot and can sustain a lot more damage than you probably can in real life? The same principle applies here. Using the scan-analyze command helpfully tells you how many open ports connected computers have and how much hacking skill it will require to break in. That’d be handy in real life, we bet.
We did think it was bad form that the tutorial admonished us for not entering the commands it wanted us to. What kind of hacker wouldn’t try something else? Anyway, it’s probably a better diversion than whatever Facebook or phone game your friends are wasting time with. It probably doesn’t impart any real hacking skills, but not everything has to be useful.
If you want a game that might teach you something, try the Bash crawl adventure. Or, go write and play some BASIC games in your browser.



 Lexicographic research comes from huge corpora, databases of tens or hundreds of millions of words of written English, from which they can extract the subtlest of language trends to see where a word is going. These can be interesting and engrossing tools for anyone, not just linguists, so we’d urge you to
Lexicographic research comes from huge corpora, databases of tens or hundreds of millions of words of written English, from which they can extract the subtlest of language trends to see where a word is going. These can be interesting and engrossing tools for anyone, not just linguists, so we’d urge you to 
![[Paul] showing off some of the Pimoroni attention to design detail. This artwork is hidden behind a display panel on the finished product.](https://hackaday.com/wp-content/uploads/2018/05/pimoroni-paul.jpg?w=400)













