[Laxman] was poking around Facebook looking for security vulnerabilities. Facebook runs a bug bounty program which means if you can find a vulnerability that’s serious enough, it can earn you cold hard cash. It didn’t take much for [Laxman] to find one worthy of a bounty.
The graph API is the primary way for Facebook apps to read and write to the Facebook social graph. Many apps use this API, but there are limitations to what it can do. For example, the API is unable to delete users’ photo albums. At least, it’s not supposed to be able too. [Laxman] decided to test this claim himself.
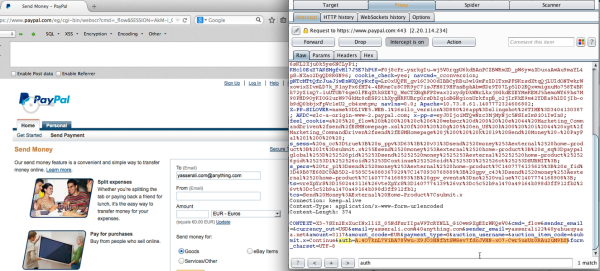
He started by sending a command to delete one of his own albums using a graph explorer access token. His request was denied. The application didn’t have the correct permissions to be able to perform that action. It seemed that Facebook was correct and the API was unable to delete photos. [Laxman] had another trick up his sleeve, though. He noticed that the wording of the response suggested that other apps would have the ability to delete the albums, so he decided to check the Facebook mobile application.
He decided to send the same request with a different token. This time he used a token from the Facebook for Mobile application. This actually worked, and resulted in his photo album being deleted. To take things a step further, [Laxman] sent the same requests, but changed the user’s ID to a victim account he had set up. The request was accepted and processed without a problem. This meant that [Laxman] could effectively delete photo albums from any other user without that user’s consent. The vulnerability did require that [Laxman] had permission to view the album in the first place.
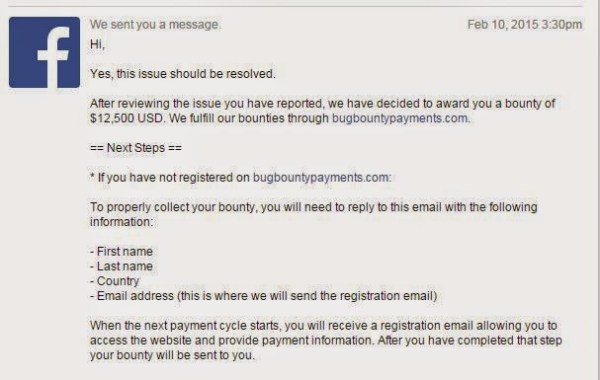
Since [Laxman] is one of the good guys, he sent this bug in to the Facebook team. It took them less than a day to fix the issue and they rewarded [Laxman] $12,500 for his trouble. It’s always nice to be appreciated. The video below shows [Laxman] walking through how he pulled off this hack using Burp Suite. Continue reading “Deleting Facebook Albums Without Permission”