Delicious sheets of wallboard coated with yummy latex paints, all kept warm and moist by a daily deluge of showers and habitually forgetting to turn on the bathroom exhaust fan. You want mildew? Because that’s how you get mildew.
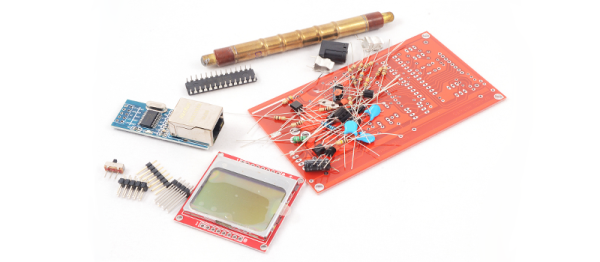
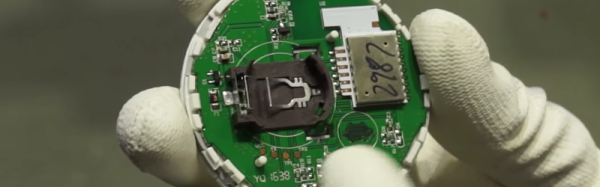
Fed up with the fuzzy little black spots on the ceiling, [Innovative Tom] decided to make bathroom ventilation a bit easier with this humidity-sensing IoT control for his bathroom exhaust fan. Truthfully, his build accomplishes little more than a $15 timer switch for the fan would, with one critical difference — it turns the fan on automatically when the DHT11 sensor tells the WeMos board that the relative humidity has gone over 60%. A relay shield kicks the fan on until the humidity falls below a set point. A Blynk app lets him monitor conditions in the bathroom and override the automatic fan, which is handy for when you need it for white noise generation more than exhaust. The best part of the project is the ample documentation and complete BOM in the description of the video below, making this an excellent beginner’s project.
No bathroom fan? Not a problem — this standalone humidity-sensing fan can help. Or perhaps you have other bathroom ventilation needs that this methane-sensing fan could help with?
Continue reading “Fight Mold And Mildew With An IoT Bathroom Fan”