We’re guessing that we have something in common with a substantial number of our readers in that this post is being written on an open-source operating system. A well-known GNU/Linux distribution provides everything you might expect from a PC, but of course it’s not the only open-source game in town. A year-old piece from [Unixsheikh] caught the eye with the title “Why you should migrate everything from Linux to BSD“, and being naturally curious, it was worth a read. It’s interesting enough to talk about here not because of its BSD advocacy, but because of its examination of some of GNU/Linux’s shortcomings. Using and appreciating an operating system shouldn’t mean slavish fandom, it’s worth every Linux user taking a moment to consider its points. Continue reading “Holding A Mirror Up In Front Of GNU/Linux”
linux673 Articles
Why Blobs Are Important, And Why You Should Care
We are extraordinarily fortunate to live at a time in which hardware with astounding capabilities can be had for only a few dollars. Systems that would once have taken an expensive pile of chips and discretes along with months of development time to assemble are now integrated onto commodity silicon. Whether it is a Linux-capable system-on-chip or a microcontroller, such peripherals as WiFi, GPUs, Bluetooth, or USB stacks now come as part of the chip, just another software library rather than a ton of extra hardware.
Beware The Blob!
If there is a price to be paid for this convenience, it comes in the form of the blob. A piece of pre-compiled binary software that does the hard work of talking to the hardware and which presents a unified API to the software. Whether you’re talking to the ESP32 WiFi through an Arduino library or booting a Raspberry Pi with a Linux distribution, while your code may be available or even maybe open source, the blob it relies upon to work is closed source and proprietary. This presents a challenge not only to Software Libre enthusiasts in search of a truly open source computer, but also to the rest of us because we are left reliant upon the willingness of the hardware manufacturer to update and patch their blobs.
An open-source advocate would say that the solution is easy, the manufacturers should simply make their blobs open-source. And it’s true, were all blobs open-source then the Software Libre crowd would be happy and their open-source nature would ease the generation of those updates and patches. So why don’t manufacturers release their blobs as open-source? In some cases that may well be due to a closed-source mindset of never releasing anything to the world to protect company intellectual property, but to leave it at that is not a full answer. To fully understand why that is the case it’s worth looking at how our multifunctional chips are made.
Continue reading “Why Blobs Are Important, And Why You Should Care”
What’s The Deal With Chromium On Linux? Google At Odds With Package Maintainers
Linux users are more likely than most to be familiar with Chromium, Google’s the free and open source web project that serves as the basis for their wildly popular Chrome. Since the project’s inception over a decade ago, users have been able to compile the BSD licensed code into a browser that’s almost the same as the closed-source Chrome. As such, most distributions offer their own package for the browser and some even include it in the base install. Unfortunately, that may be changing soon.
A post made earlier this month to the official Chromium Blog explained that an audit had determined “third-party Chromium based browsers” were using APIs that were intended only for Google’s internal use. In response, any browser attempting to access features such as Chrome Sync with an unofficial API key would be prevented from doing so after March 15th.
To the average Chromium user, this doesn’t sound like much of a problem. In fact, you might even assume it doesn’t apply to you. The language used in the post makes it sound like Google is referring to browsers which are spun off of the Chromium codebase, and at least in part, they are. But the search giant is also using this opportunity to codify their belief that the only official Chromium builds are the ones that they provide themselves. With that simple change, anyone using a distribution-specific build of Chromium just became persona non grata.
Unhappy with the idea of giving users a semi-functional browser, the Chromium maintainers for several distributions such as Arch Linux and Fedora have said they’re considering pulling the package from their respective repositories altogether. With a Google representative confirming the change is coming regardless of community feedback, it seems likely more distributions will follow suit.
Continue reading “What’s The Deal With Chromium On Linux? Google At Odds With Package Maintainers”
A Fresh Linux For The Most Unexpected Platform – The Nintendo 64
Though it was famously started by Linus Torvalds as “a (free) operating system (just a hobby, won’t be big and professional like gnu) for 386(486) AT clones“, the Linux kernel and surrounding operating system ecosystems have been ported to numerous architectures beyond their x86 roots. It’s therefore not unusual to hear of new ports for unsupported platforms, but it is extremely unexpected to hear of one when the platform is a games console from the mid-1990s. But that’s what [Lauri Kasanen] has done, announcing a fresh Linux port for the Nintendo 64.
This isn’t a Linux from 1996 either. The port builds on an up-to-date kernel version 5.10 with his N64 branch and a tantalising possibility that it might be incorporated into the main Linux source for the MIPS-64 processor architecture. That’s right, the Nintendo 64 could be an officially supported Linux platform.
It would be stretching the story a long way to call this any kind of distro, for what he’s produced is a bootloader that loads the kernel and creates a terminal with busybox loaded. With this on your flashcart you won’t be replacing that Raspberry Pi any time soon, so why other than [Lauri]’s “because I can” would you be interested in it? He supplies the answer and it lies in the emulation scene, because having a Linux for the platform makes it so much easier to port other software to it. If this tickles your fancy you can see the source in his GitHub repository, and we’re certainly looking forward to what the community will do with it.
We are more used to seeing the N64 as a subject for case-modding, whether it be as a handheld or a an all-in-one console.
Via Phoronix, and thanks [David Beckershoff] for the tip.
Header image: Evan-Amos, Public domain.
BASH Template Promises Safer Scripts
Many bash scripts start out as something quick and dirty but then become so useful that they live for years, indeed sometimes seeing more use than our traditional programs. Now that you can even run bash well under Windows (although, you’ve always been able to run it there if you tried), there are even more opportunities for your five-minute bash script to proliferate. [Maciej] decided he was tired of always having to patch up his quick and dirty scripts to be more robust, so he created (and shared) his boilerplate template for scripts.
Probably most of us have at least some basic template we start with, even if it just our last script project. What’s nice about [Maciej’s] template is that he documents what’s going on with each part of it. It is also relatively short without a lot of excess stuff. Of course, you’ll probably customize it, but it is a great place to start.
Linux Fu: VPN For Free With SSH
If you see a lot of banner ads on certain websites, you know that without a Virtual Private Network (VPN), hackers will quickly ravage your computer and burn down your house. Well, that seems to be what they imply. In reality, though, there are two main reasons you might want a VPN connection. You can pay for a service, of course, but if you have ssh access to a computer somewhere on the public Internet, you can set up your own VPN service for no additional cost.
The basic idea is that you connect to a remote computer on another network and it makes it look like all your network traffic is local to that network. The first case for this is to sidestep or enhance security. For example, you might want to print to a network printer without exposing that printer to the public Internet. While you are at the coffee shop you can VPN to your network and print just like you were a meter away from the printer at your desk. Your traffic on the shop’s WiFi will also be encrypted.
The second reason is to hide your location from snooping. For example, if you like watching the BBC videos but you live in Ecuador, you might want to VPN to a network in the UK so the videos are not blocked. If your local authorities monitor and censor your Internet, you might also want your traffic coming from somewhere else.
MicroOS Is Immutable Linux
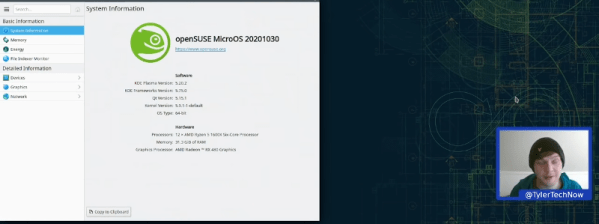
Linux finds a lot of uses in computers that aren’t desktops. But there is a problem. What happens if your mission-critical control computer or retail kiosk gets an update and then fails? Happens all the time with Windows and it can happen with Linux, too. The openSUSE project has an answer: MicroOS which bills itself as immutable. Aimed at container deployment, the operating system promises atomic updates with no disk changes during runtime. If an update does break something, the BTRFS file system allows you to roll back to a previous snapshot. [Tyler] installs the OS and gives it a walkthrough in the video below.
As [Tyler] found, there are not many applications installed by default. Instead, you are expected to install flatpaks so the applications live in their own containers, isolated from the operating system and each other.