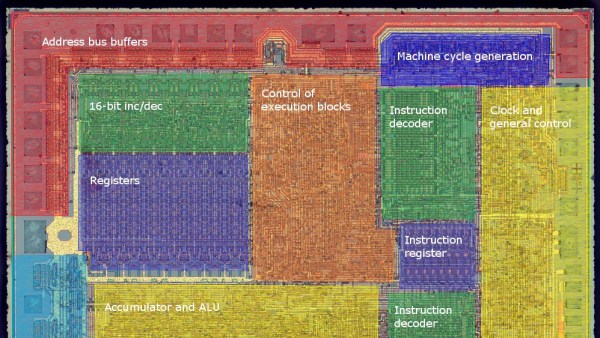
The folks at Zeptobars are on a roll, sometimes looking deep inside historic chips and at others exposing fake devices for our benefit. Behind all of those amazing die shots are hundreds of hours of hard work. [Mikhail] from Zeptobars recently tipped us off on the phenomenal work done by engineer [Vslav] who spent over 1000 hours reverse engineering the Soviet KR580VM80A – one of the most popular micro-controllers of the era and a direct clone of the i8080.
But before [Vslav] could get down to creating the schematic and Verilog model, the chip needed to be de-capped and etched. As they etched down, they created a series of high resolution images of the die. At the end of that process, they were able to determine that the chip had exactly 4758 transistors (contrary to rumors of 6000 or 4500). With the images done, they were able to annotate the various parts of the die, create a Verilog model and the schematic. A tough compatibility test confirmed the veracity of their Verilog model. All of the source data is available via a (CC-BY-3.0) license from their website. If this looks interesting, do check out some of their work that we have featured earlier like comparing real and fake Nordic dies and amazing descriptions of how they figure out the workings of these decapped chips. If this is too deep for you check out the slightly simpler but equally awesome process of delayering PCBs.