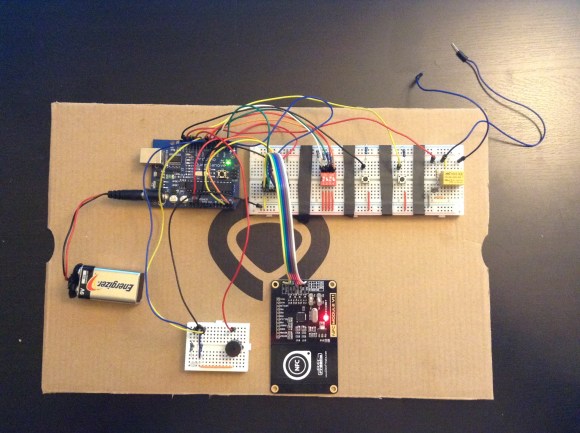
[Jason] really wanted to build an RFID controlled garage door opener and decided to turn to Arduino to get the job done. For someone who’s never worked with an Arduino before, he really seemed to know what he was doing.
The Arduino acts as the brains of the operation while an off-the-shelf NFC/RFID reader module is used to read the RFID tags. To add new keys to the system, [Jason] simply swipes his “master” RFID key. An indicator LED lights up and a piezo speaker beeps, letting you know that the system is ready to read a new key. Once the new key is read, the address is stored on an EEPROM. From that point forward the new key is permitted to activate the system.
Whenever a valid key is swiped, the Arduino triggers a relay which can then be used to control just about anything. In this case, [Jason] plans to use it to control his garage door. The system also has a few manual controls. First is the reset button. If this button is held down for two seconds, all of the keys from the EEPROM are erased. This button would obviously only be available to people who are already inside the garage. There is also a DIP switch that allows the user to select how long the relay circuit should remain open. This is configurable in increments of 100ms.
For now the circuit is wired up on a couple of breadboards, but it might be a good idea to use something more permanent. [Jason] could always take it a step further and learn to etch his own PCB’s. Or he could even design a board in Eagle CAD and order a real printed board. Don’t miss the video description of the RFID system below. Continue reading “Upgrade Your Garage Door With Arduino And RFID”