[Pong] has joined an elite club of people who have designed and built their own computer – including a CPU created from discrete 7400 series logic. His computer is the Almost Simple As Possible Computer 3 (ASAP-3). ASAP-3 is not a completely new design. The architecture is based upon the SAP series of computers from Albert Malvino’s book, Digital Computer Electronics. [Pong] looked at quite a few of the “modern retro” computers such as Magic-1, Big Mess o’ Wires 1, and the Duo. These computers were beyond his skill levels back then, so he began to build his own system. His primary design goal was to be able to run a 4 function calculator program.
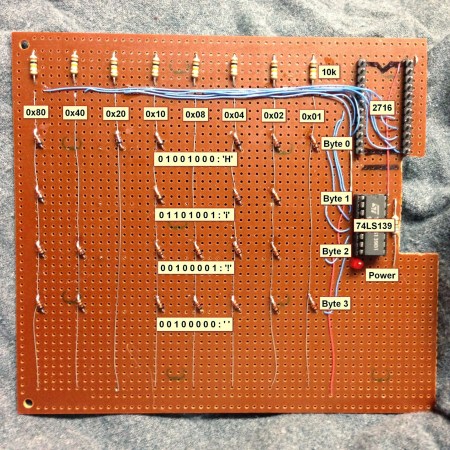
One thing that can’t be stressed enough is the fact that [Pong] made his design work much easier by using lots of simulation. His tool of choice was Proteus Design Suite. While simulation can’t solve every problem, it can often help in verifying that a given design is sound. The ASAP-3’s instruction set is microcode, based upon the 8085 series instruction set. The microcode itself is stored on Flash ROMS. Using microcode makes ASAP-3 very flexible. Don’t have a machine instruction you need? No problem – just write one up. When all was said and done, [Pong] had over 100 instructions spread over 3 Flash ROM chips.
The hardware was only half the battle – [Pong] found writing the software just as challenging. He wrote all the software by hand in his own machine code. This is where the simulation mentioned above really saved him some time. Even with simulation he still ran into some problems. The ASAP-1 is limited to a clock speed of around 500kHz. Above that, glitches from the ROM chips start triggering the asynchronous inputs in some of the registers. [Pong] doesn’t have a logic analyzer on hand, so he wasn’t able to track this one down further. He also found a (update simulation only) issue with the carry bit on the 74LS181 bit slice ALU. In certain circumstances the carry bit would not propagate correctly. [Pong] corrected this by using a ROM as a look up table replacement for certain ‘181 functions. Even with these limitations, this is still a great hack!
Continue reading “ASAP 3 – The Almost Simple As Possible Computer”