![]()
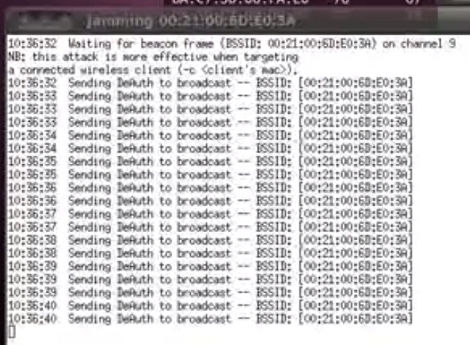
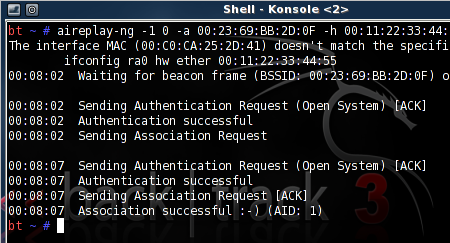
While we can’t condone the actual use of this device, [Husam]’s portable WiFi jammer is actually pretty cool. It uses a Raspberry Pi and an Aircrack-ng compatible dongle to spam the airwaves with deauth packets. The entire device is packaged in a neat box with an Arduino-controlled LCD and RGB LEDs. Check out an imgur gallery here.
You can pick up a wireless phone charger real cheap from any of the usual internet outlets, but try finding one that’s also a phone stand. [Malcolm] created his own. He used a Qi charger from DealExtreme and attached it to a 3D printed phone stand.
A while back, [John] noticed an old tube radio in an antique store. No, he didn’t replace the guts with a Raspberry Pi and an SD card full of MP3s. He just brought it back to working condition. After fixing the wiring (no ground cord on these old things), repairing the speaker cone, putting some new twine on the tuner and replacing the caps, [John] has himself a new old radio. Here’s a video of the complete refurbishment.
Here’s a Sega Master System (pretty much a Game Gear) running on an STM32 dev board. Also included are some ROMs for some classic games – Sonic the Hedgehog, Castle of Illusion, and The Lion King. If you have this STM Discovery board you can grab the emulator right here.
[Spencer] wanted a longer battery life in his iPhone, so he did what any engineering student would do: he put another battery in parallel.
Breadboarding something with an AVR or MAX232? Print out some of these stickers and make sure you get the pinouts right. Thanks, [Marius].