There was a time around two decades ago, when the new hotness was taking control of home routers to use as small Linux computers. An echo of this era lives on in the name of the OpenWrt minimal Linux distribution, in reference to the Linksys WRT54G router which started it all. Routers as small computers were displaced by small cheap Linux machines from the likes of Raspberry Pi, and the promise of discarded home network gear doing interesting stuff receded. Now it might just be back, as [Jasper Devreker] shows us an Android TV set-top box from a mobile carrier repurposed as a Linux computer that can even run a desktop environment.
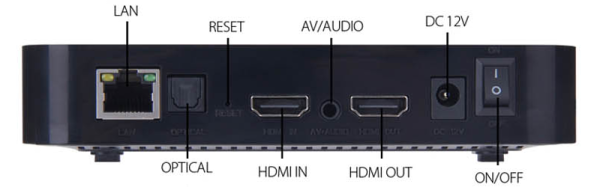
The method starts as you might expect, by identifying a mystery connector as a debug serial port. This outputs all sorts of interesting boot information, but can be dropped into a uBoot shell. From here with a bit of effort the eMMC storage could be dumped, and from that the nature of the machine could be deduced. The CPU is an Amlogic quad core ARM Cortex-A53 SoC, which by a stroke of luck is a target for which an Armbian build is available. From there a Linux installation could be assembled, and even an AFCE desktop.
These boxes are handed out in the hundreds of thousands by home connectivity providers, so there’s value in this type of hack as they become available for experimenters. Perhaps it’s more useful as a small headless Linux machine than as a desktop, but we sense there are more machines to come in this line.
If you’d like a little bit of history on hackable Linux devices, have a read of one of our earliest posts featuring the Linksys WRT54G.