While the cost of a hobby-grade remote control transmitter has dropped significantly over the last decade or so, even the basic models are still relatively expensive. It’s not such a big deal if you only need to get one for personal use, but for a school to outfit a classroom’s worth of students their own radios, they’d need to have a serious STEM budget.
Which is why [Miharix], himself an educator with a decade of experience, developed a project that leverages the ESP8266 to create affordable RC vehicles that can be controlled with a smartphone’s web browser. There’s a bit of irony at play since the smartphones are more expensive than the RC transmitters would have been; but with more and more school-age kids having their own mobile devices, it takes the cost burden off of the educators. Depending on the age of the students, the teacher would only need to keep a couple of burner phones on hand for student that doesn’t have a device of their own.
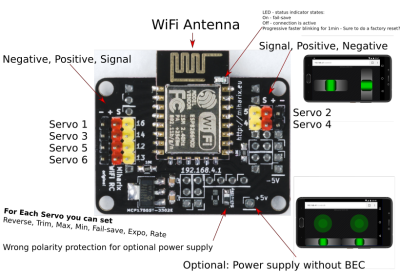
In its fully realized form, the project uses an open hardware board that allows standard RC hobby servos to be connected to the GPIO pins of a ESP-12E module. But if you don’t want to go through the trouble of building the custom hardware, you could put something similar together with an ESP development board. From there it’s just a matter of installing the firmware, which starts up a server providing a touch-based controller interface that’s perfect for a smartphone’s screen.
Since the ESP8266 pops up as an Access Point that client devices can connect to, you don’t even need to have an existing network in place. Or Internet access, for that matter. [Miharix] says that in tests, the range between a common smartphone and the ESP8266 is approximately 85 meters (260 feet), which should be more than enough to get the job done.
In the videos after the break you can see this system being used with an RC car and boat, though the only limit to what you could control with this project is your own imagination.














