It’s long been common wisdom that one of the safest places to keep your cryptocurrency holdings is in a hardware wallet. These are small, portable devices that encrypt your keys and offer a bit more peace of mind than holding your coins in a soft or web wallet.
But of course, as we know, nothing is totally secure.
And we were reminded of this fact by Kraken Security Labs, when they showed us how they bypassed all of the safeguards in a popular wallet, the Trezor, to dump and decrypt it’s seed.
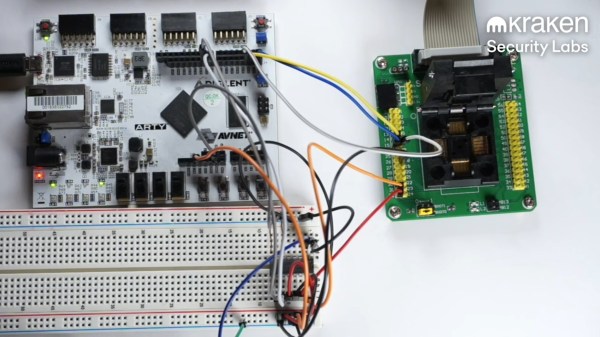
It’s worth noting that the hack does require physical access to the wallet — albeit only about fifteen minutes worth. And by “physical access” we mean that the hack leaves the device thoroughly mutilated. The Kraken team started by desoldering the heart of the wallet, a STM32 processor. They then dropped it into a socket on an interface board, and got to glitching.
The hack relies on an attack known as voltage glitching. Essentially, at a precisely-timed moment during the device’s boot sequence, the supply voltage is fluctuated. This enables the chip’s factory bootloader, which can read out the contents of it’s onboard flash memory. The memory is read-protected, but can be accessed 256 bytes at a time through a second voltage glitch. Neither of these attacks work 100% of the time, so if the device fails to boot or the memory remains locked, the FPGA performing the attacks simply tries again. After enough iterations, the Kraken team was able to fully dump the chip’s flash memory.
Continue reading “Hacking Hardware Bitcoin Wallets: Extracting The Cryptographic Seed From A Trezor”







 usually to move a tool head in such a way as to make something. Tons of systems have been built around it, including early Makerbot printers.
usually to move a tool head in such a way as to make something. Tons of systems have been built around it, including early Makerbot printers.








