Flip-dot displays look and sound awesome. At least to all of us electronics geeks who dumpster dive for second-hand panels to add to our collections of esoteric display technology. But there are people thinking beyond the yellow/white dots on a black background. [BreakfastNY] have produced a new take on what a flip-dot display can be with color and a bit of theatrics.
Mechanically these are standard pixels that use an electromagnetic coil to pivot a disc between two states. But immediately you’ll see the inert display has a mosaic printed right on the dots. It gets even more fun to realize the same image is present on the rear of the dots but in a different color palette. In the case of this piece, entitled Empire State, it looks like a sunny day on one side and an overcast day on the reverse.
We wondered what this art collective was up to when they began selling flip-dot modules they had designed back in 2016. Having those kinds of connections meant they were able to sweet-talk their manufacturing partners into custom printing colors on the discs during manufacture. The group continues to use their camera-based interactivity that represents silhouettes on the display. The innovative color palette still lets that work quite well, but one really interesting animation choice here is an indeterminate flutter of the pixels. It builds a Matrix-style waterfall animating into the image, beckoning the viewer to walk over with the ulterior motive that this brings them within camera range.
If you want to give the flutter effect a try for yourself, you might want to peek at the 30 FPS flip-dot driver we saw a few weeks back as a responsive option.





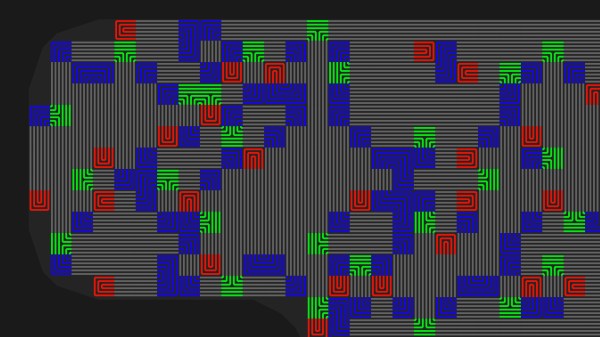
 The idea is pretty simple, place traces very close to one another and it makes it impossible to drill into the case of a device without upsetting the apple cart. There are other uses as well, such as embedding them in adhesives that destroy the traces when pried apart. For [Sebastian’s] experiments he’s sticking with PCBs because of the ease of manufacture. His plugin lays down a footprint that has four pads to begin and end two loops in the mesh. The plugin looks for an outline to fence in the area, then uses a space filling curve to generate the path. This proof of concept works, but it sounds like there are some quirks that can crash KiCad. Consider
The idea is pretty simple, place traces very close to one another and it makes it impossible to drill into the case of a device without upsetting the apple cart. There are other uses as well, such as embedding them in adhesives that destroy the traces when pried apart. For [Sebastian’s] experiments he’s sticking with PCBs because of the ease of manufacture. His plugin lays down a footprint that has four pads to begin and end two loops in the mesh. The plugin looks for an outline to fence in the area, then uses a space filling curve to generate the path. This proof of concept works, but it sounds like there are some quirks that can crash KiCad. Consider