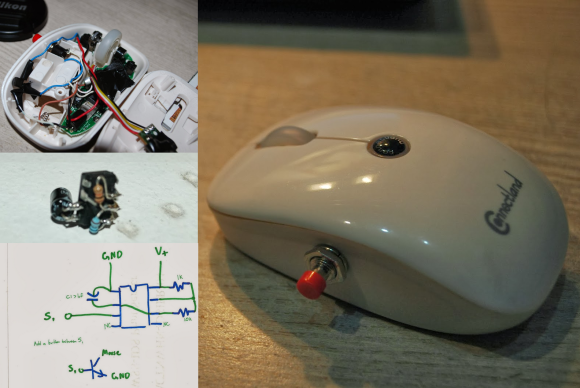
[Peter Skaarup’s] been re-living the past by playing old-school games in DOSBox. He’s using a mouse as the controller but longed for the auto-fire button that many joysticks used to have. Instead of looking around for a gamepad with this feature he decided to add an auto-fire button to the mouse. He incorporated a PIC 10F200, along with a momentary push switch and a transistor. The push switch enables the autofire feature, causing the transistor to short the left mouse button about seventeen times a second. Problem solved, and with a couple of other pins on the microcontroller there’s room for this project to grow.
Interested in an auto-fire feature for your gaming console? Perhaps this Xbox 360 rapid fire mod will give you some inspiration.