Although laser communication in space is far from novel, its wide-scale deployment as seen with SpaceX’s Starlink satellite internet constellation has brought the technology to the forefront like never before. This was quite apparent during the SPIE Photonics West event on January 30th when [Michael Kan] and other journalists attended a presentation by SpaceX’s [Travis Brashears] on the inter-satellite laser communication performance that was first enabled with the Starlink v1.5 satellites.
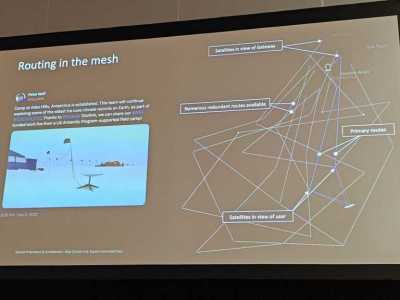
Among currently active inter-satellite communication systems, Starlink is by far the most numerous and with the highest bandwidth, reaching over 42 PB per day across its over 9000 space lasers (yes, that is over 9000) for a 5.6 Tbps throughput. Since these satellites form a mesh network with their 100 Gbps laser transceivers, a big part of using it efficiently is to route any data with the least amount of latency while taking into account link distance (maximum of 5,400 km), link duration (up to multiple weeks) and presence of other Starlink satellites before they become within reach. With this complex mesh in LEO, this also means that a very high uptime can be accomplished, with a claimed 99.99% due to rapid route changing.
For the future, SpaceX has plans to not only keep upgrading its own Starlink satellites with better laser transceivers, but to also make them available to third-party satellites, as well as beam the lasers directly down to Earth for ground-based transceivers. The latter is still cutting edge, despite it being tested to beam cat videos to Earth from Deep Space.