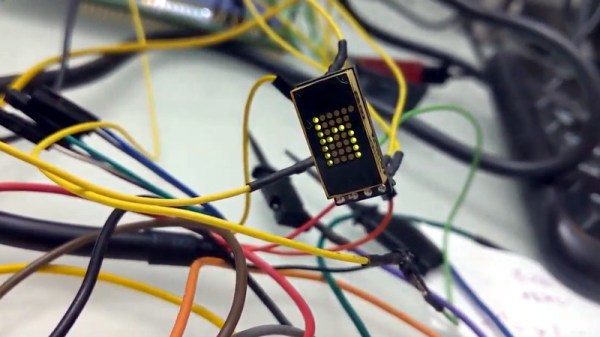
Used in everything from calculators to military hardware, the 3LS363A is an interesting piece of vintage hardware. With a resolution of 5 x 7 (plus a decimal point), the Soviet-made displays contain no electronics and are simply an array of 36 green LEDs. It’s not hard to drive one of them in a pinch, but [Dmitry Grinberg] thought this classic device deserved a bit better than the minimum.
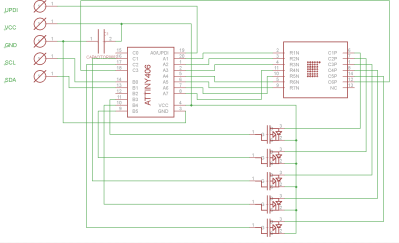 He’s developed a small board that sits behind the 3LS363A and allows you to control it over I2C for a much more modern experience when working with these vintage displays. Powered by the ATtiny406, his adapter board makes it easy to chain the modules together and even handles niceties like flipping the displayed image to account for different mounting positions. While most of us probably won’t have the chance to play around with these relatively rare displays, there’s still plenty of useful information here if you’re thinking of creating your own I2C gadgets.
He’s developed a small board that sits behind the 3LS363A and allows you to control it over I2C for a much more modern experience when working with these vintage displays. Powered by the ATtiny406, his adapter board makes it easy to chain the modules together and even handles niceties like flipping the displayed image to account for different mounting positions. While most of us probably won’t have the chance to play around with these relatively rare displays, there’s still plenty of useful information here if you’re thinking of creating your own I2C gadgets.
In his write-up, [Dmitry] explains his rationale behind the design and some of the quirks of working with the display. For example he explains how he gave each column of the display its own FET, but to save space on the board ended up running the single decimal point (technically its own column) directly off of a spare GPIO pin. Relying on the low duty cycle, he even left current limiting resistors off the design. The end result is a tiny board that keeps the same footprint of the 3LS363A itself.
[Dmitry] went all out with developing the firmware for his new “smart” 3LS363A displays, and has written up documentation for the different commands he has implemented. From re-configuring the I2C address to updating the firmware, he’s made sure no stone was left unturned for this project. We’re not ones to shy away from a quick and dirty code, but it’s always nice to see when somebody has really put some thought into the software side of a project.
We’ve seen our fair share of oddball Soviet displays here at Hackaday, utilizing everything from heavy duty incandescent bulbs to remarkably tiny “intelligent” LEDs. While it’s unlikely any of them will dethrone the nixie as king of the retro display devices, it’s always interesting to see unusual hardware being used in the wild.