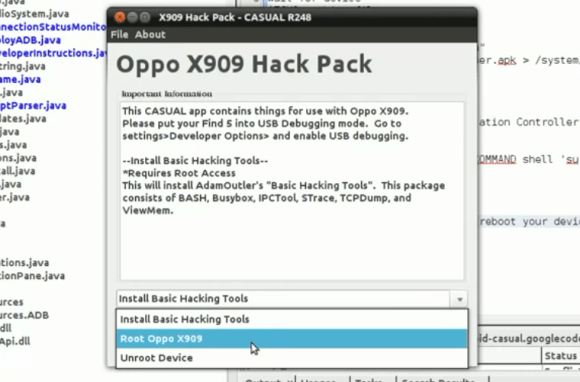
[Adam Outler] tipped us off about a cross-platform Android hacking suite he’s been working on. The project, which is called CASUAL, brings several things to the table. First and foremost it breaks down the OS requirements seen on some hacks. It can perform pretty much any Android hack out there and it doesn’t care if you’re using Linux, OS X, or Windows.
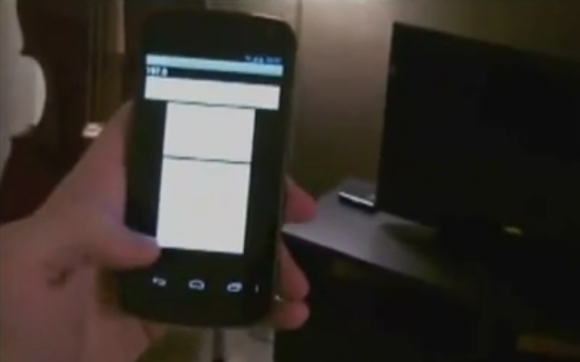
We’ve embedded two videos after the break. The screenshot seen above is from the first clip where [Adam] demonstrates the package rooting the Oppo Find5 Android phone. He then goes on to show off the scripting language CASUAL uses. This layer of abstraction should make it easier to deploy hacking packages, as CASUAL handles all of the underlying tools like the Android Debug Bridge, fastboot, and Heimdall (an open source Odin replacement which brings the low level tool to all OS platforms) . The second video demonstrates a Galaxy Note II being rooted, and having a new recovery image flashed.
Continue reading “CASUAL Seeks To Make Android Hacking OS Agnostic”