Remember the Key Bridge collapse? With as eventful a year as 2025 has been, we wouldn’t blame anyone for forgetting that in March of 2024, container ship MV Dali plowed into the bridge across Baltimore Harbor, turning it into 18,000 tons of scrap metal in about four seconds, while taking the lives of six very unlucky Maryland transportation workers in the process. Now, more than a year and a half after the disaster, we finally have an idea of what caused the accident. According to the National Transportation Safety Board’s report, a loss of electrical power at just the wrong moment resulted in a cascade of failures, leaving the huge vessel without steerage. However, it was the root cause of the power outage that really got us: a wire with an incorrectly applied label.
Hackaday Columns4664 Articles
This excellent content from the Hackaday writing crew highlights recurring topics and popular series like Linux-Fu, 3D-Printering, Hackaday Links, This Week in Security, Inputs of Interest, Profiles in Science, Retrotechtacular, Ask Hackaday, Teardowns, Reviews, and many more.
Retrotechtacular: Computers In Schools? 1979 Says Yes
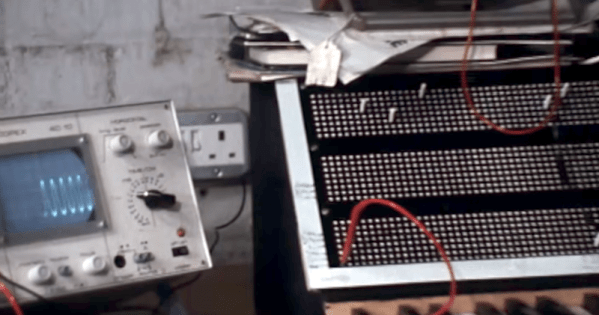
The BBC wanted to show everyone how a computer might be used in schools. A program aired in 1979 asks, “Will Computers Revolutionise Education?” There’s vintage hardware and an appearance of PILOT, made for computer instructions.
Using PILOT looks suspiciously like working with a modern chatbot without as much AI noise. The French teacher in the video likes that schoolboys were practicing their French verb conjugation on the computer instead of playing football.
If you want a better look at hardware, around the five-minute mark, you see schoolkids making printed circuit boards, and some truly vintage oscilloscope close-ups. There are plenty of tiny monitors and large, noisy printing terminals.
You have to wonder where the eight-year-olds who learned about computers in the video are today, and what kind of computer they have. They learned binary and the Towers of Hanoi. Their teacher said the kids now knew more about computers than their parents did.
As a future prediction, [James Bellini] did pretty well. Like many forecasters, he almost didn’t go far enough, as we look back almost 50 years. Sure, Prestel didn’t work out as well as they thought, dying in 1994. But he shouldn’t feel bad. Predicting the future is tough. Unless, of course, you are [Arthur C. Clarke].
Continue reading “Retrotechtacular: Computers In Schools? 1979 Says Yes”
Why Do We Love Weird Old Tech?
One of our newer writers, [Tyler August], recently wrote a love letter to plasma TV technology. Sitting between the ubiquitous LCD and the vanishing CRT, the plasma TV had its moment in the sun, but never became quite as popular as either of the other display techs, for all sorts of reasons. By all means, go read his article if you’re interested in the details. I’ll freely admit that it had me thinking that I needed a plasma TV.
I don’t, of course. But why do I, and probably a bunch of you out there, like old and/or odd tech? Take [Tyler]’s plasma fetish, for instance, or many people’s love for VFD or nixie tube displays. At Supercon, a number of people had hit up Apex Electronics, a local surplus store, and came away with some sweet old LED character displays. And I’ll admit to having two handfuls of these displays in my to-hack-on drawer that I bought surplus a decade ago because they’re so cute.
It’s not nostalgia. [Tyler] never had a plasma growing up, and those LED displays were already obsolete before the gang of folks who had bought them were even born. And it’s not simply that it’s old junk – the objects of our desire were mostly all reasonably fancy tech back in their day. And I think that’s part of the key.
My theory is that, as time and tech progresses, we see these truly amazing new developments become commonplace, and get forgotten by virtue of their ever-presence. For a while, having a glowing character display in your car stereo would have been truly futuristic, and then when the VFD went mainstream, it kind of faded into our ambient technological background noise. But now that we all have high-res entertainment consoles in our cars, which are frankly basically just a cheap tablet computer (see what I did there?), the VFD becomes an object of wonder again because it’s rare.
Which is not to say that LCD displays are anything short of amazing. Count up the rows and columns of pixels, and multiply by three for RGB, and that’s how many nanoscale ITO traces there are on the screen of even the cheapest display these days. But we take it for granted because we are surrounded by cheap screens.
I think we like older, odder tech because we see it more easily for the wonder that it is because it’s no longer commonplace. But that doesn’t mean that our current “boring” tech is any less impressive. Maybe the moral of the story is to try to approach and appreciate what we’ve got now with new eyes. Pretend you’re coming in from the future and finding this “old” gear. Maybe try to figure out how it must have worked.
Hackaday Podcast Episode 346: Melting Metal In The Microwave, Unlocking Car Brakes And Washing Machines, And A Series Of Tubes
Wait, what? Is it time for the podcast again? Seems like only yesterday that Dan joined Elliot for the weekly rundown of the choicest hacks for the last 1/52 of a year. but here we are. We had quite a bit of news to talk about, including the winners of the Component Abuse Challenge — warning, some components were actually abused for this challenge. They’re also a trillion pages deep over at the Internet Archive, a milestone that seems worth celebrating.
As for projects, both of us kicked things off with “Right to repair”-adjacent topics, first with a washing machine that gave up its secrets with IR and then with a car that refused to let its owner fix the brakes. We heated things up with a microwave foundry capable of melting cast iron — watch your toes! — and looked at a tiny ESP32 dev board with ludicrously small components. We saw surveyors go to war, watched a Lego sorting machine go through its paces, and learned about radar by spinning up a sonar set from first principles.
Finally, we wrapped things up with another Al Williams signature “Can’t Miss Articles” section, with his deep dive into the fun hackers can have with the now-deprecated US penny, and his nostalgic look at pneumatic tube systems.
This Week In Security: Cloudflare Wasn’t DNS, BADAUDIO, And Not A Vuln
You may have noticed that large pieces of the Internet were down on Tuesday. It was a problem at Cloudflare, and for once, it wasn’t DNS. This time it was database management, combined with a safety limit that failed unsafe when exceeded.
Cloudflare’s blog post on the matter has the gritty details. It started with an update to how Cloudflare’s ClickHouse distributed database was responding to queries. A query of system columns was previously only returning data from the default database. As a part of related work, that system was changed so that this query now returned all the databases the given user had access to. In retrospect it seems obvious that this could cause problems, but it wasn’t predicted to cause problems. The result was that a database query to look up bot-management features returned the same features multiple times.
That featurelist is used to feed the Cloudflare bot classification system. That system uses some AI smarts, and runs in the core proxy system. There are actually two versions of the core proxy, and they behaved a bit differently when the featurelist exceeded the 200 item limit. When the older version failed, it classified all traffic as a bot. The real trouble was the newer Rust code. That version of the core proxy threw an error in response, leading to 5XX HTTP errors, and the Internet-wide fallout. Continue reading “This Week In Security: Cloudflare Wasn’t DNS, BADAUDIO, And Not A Vuln”
So Long, Firefox, Part One
It’s likely that Hackaday readers have among them a greater than average number of people who can name one special thing they did on September 23rd, 2002. On that day a new web browser was released, Phoenix version 0.1, and it was a lightweight browser-only derivative of the hugely bloated Mozilla suite. Renamed a few times to become Firefox, it rose to challenge the once-mighty Microsoft Internet Explorer, only to in turn be overtaken by Google’s Chrome.
Now in 2025 it’s a minority browser with an estimated market share just over 2%, and it’s safe to say that Mozilla’s take on AI and the use of advertising data has put them at odds with many of us who’ve kept the faith since that September day 23 years ago. Over the last few months I’ve been actively chasing alternatives, and it’s with sadness that in November 2025, I can finally say I’m Firefox-free.
FLOSS Weekly Episode 855: Get In The Minecart, Loser!
This week Jonathan chats with Kevin, Colin, and Curtis about Cataclysm: Dark Days Ahead! It’s a rogue-like post-apocalyptic survival game that you can play in the terminal, over SSH if you really want to! Part of the story is a Kickstarter that resulted in a graphics tile-set. And then there’s the mods!
Continue reading “FLOSS Weekly Episode 855: Get In The Minecart, Loser!”