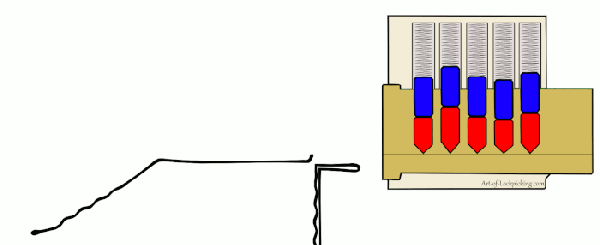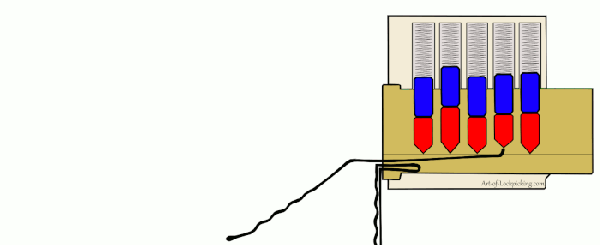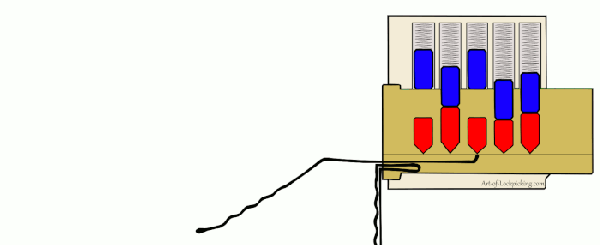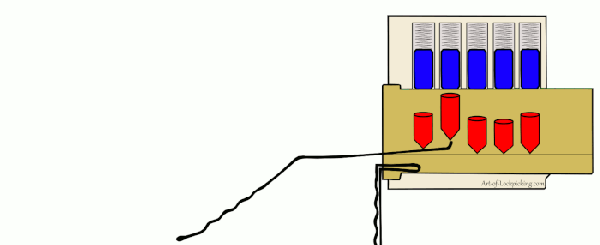
Despite what the media might tell you, picking locks isn’t just for spies and guys wearing balaclavas. Those who pick as a hobby, or even competitively, think of locks as logic puzzles. Each lock is a unique challenge, and defeating it requires patience, dexterity, and perhaps most importantly the experience that comes from regular practice. But where does one start if they want to get into the world of recreational lock picking, also known as locksport?
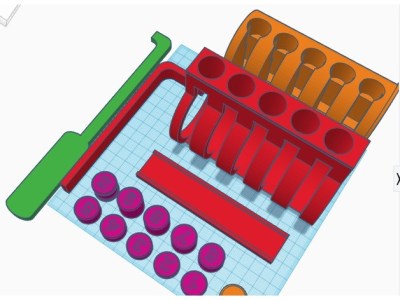 Many people begin their journey on a practice lock, usually made of clear plastic so you can see its inner-workings. That’s fine for the individual, but what if you’re trying to demonstrate lock picking to a group? [John Biggs] may have the solution for you, assuming you’ve got the time and material. His huge 3D printed cutaway lock, and appropriately sized tools, allow even the folks in the back of the room to see how basic picking techniques work.
Many people begin their journey on a practice lock, usually made of clear plastic so you can see its inner-workings. That’s fine for the individual, but what if you’re trying to demonstrate lock picking to a group? [John Biggs] may have the solution for you, assuming you’ve got the time and material. His huge 3D printed cutaway lock, and appropriately sized tools, allow even the folks in the back of the room to see how basic picking techniques work.
A print of this size is nothing to sneeze at; a quick peek on the reference printer here at the Hackaday Chamber of Secrets indicates you’re probably looking at the better part of 20 hours to print everything out. Once printed you’ll likely need to take a file and some sandpaper to all the surfaces to make sure things operate smoothly. It doesn’t appear to be a terribly challenging print all things considered, but we wouldn’t call it a beginner’s project either.
The only non-printed part in this design is the springs, which [John] mentions he hasn’t quite found the solution for yet. They need to be fairly weak or else the lock is too hard to pick, but springs large enough to work with the pins are usually pretty strong. This might be a perfect application for some custom wound springs.
After you’ve mastered the PLA lock, it might be time to make your own picks and see if anyone is giving free lock picking workshops in your area.



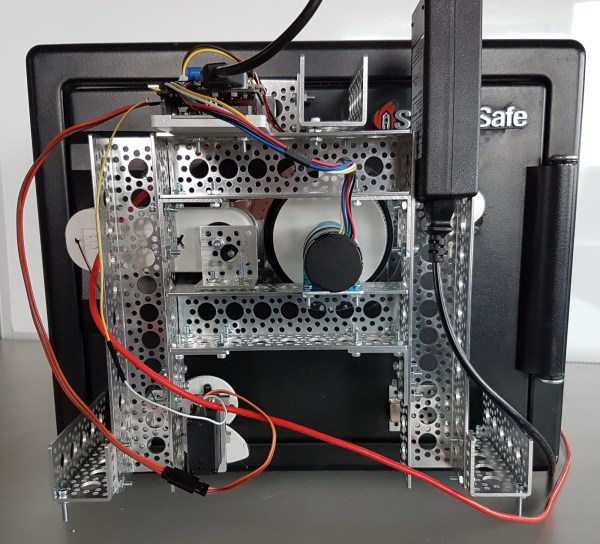
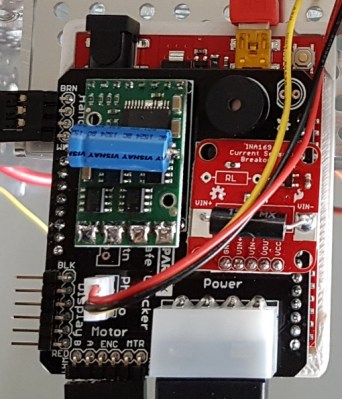
 The electronics and mechanical part of this build are pretty simple. An acrylic frame holds five solenoids over the keypad, and this acrylic frame attaches to the car with magnets. There’s a second large protoboard attached to this acrylic frame loaded up with an Arduino, character display, and a ULN2003 to drive the resistors. So far, everything you would expect for a ‘robot’ that will unlock a car via its keypad.
The electronics and mechanical part of this build are pretty simple. An acrylic frame holds five solenoids over the keypad, and this acrylic frame attaches to the car with magnets. There’s a second large protoboard attached to this acrylic frame loaded up with an Arduino, character display, and a ULN2003 to drive the resistors. So far, everything you would expect for a ‘robot’ that will unlock a car via its keypad.

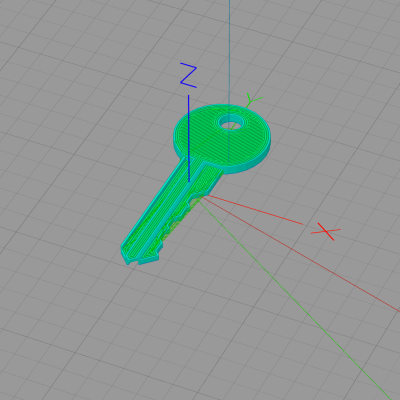 Rather than simply duplicating an existing key, [Dave] created a parametric key blank in OpenSCAD; he just enters his pin settings and the model generator creates the print file. He printed ABS on a glass plate with a schmeer of acetone on it, and .15mm layer heights. Another reason [Dave] chose Kwikset is that the one he had was super old and super loose — he theorizes that a newer, tighter lock might simply break the key.
Rather than simply duplicating an existing key, [Dave] created a parametric key blank in OpenSCAD; he just enters his pin settings and the model generator creates the print file. He printed ABS on a glass plate with a schmeer of acetone on it, and .15mm layer heights. Another reason [Dave] chose Kwikset is that the one he had was super old and super loose — he theorizes that a newer, tighter lock might simply break the key.