When you think of high-performance computing powered by NVIDIA hardware, you probably think of applications leveraging the capabilities of the company’s graphics cards. In many cases, you’d be right. But naturally there are situations where the traditional combination of x86 computer and bolt-on GPU simply isn’t going to cut it; try packing a modern gaming computer onto a quadcopter and let us know how it goes.
For these so-called “edge computing” situations, NVIDIA offers the Jetson line of ARM single-board computers which include a scaled-down GPU that gives them vastly improved performance for machine learning applications than something like the Raspberry Pi. Today during their annual GPU Technology Conference (GTC), NVIDIA announced the immediate availability of the Jetson AGX Orin Developer Kit, which the company promises can deliver “server-class AI performance” in a package small enough for use in IoT or robotics.
As with the earlier Jetsons, the palm-sized development kit acts as a sort of breakout board for the far smaller module slotted into it. This gives developers access to the full suite of the connectivity and I/O options offered by the Jetson module in a desktop-friendly form that makes prototyping the software side of things much easier. Once the code is working as intended, you can simply pop the Jetson module out of the development kit and install it in your final hardware.
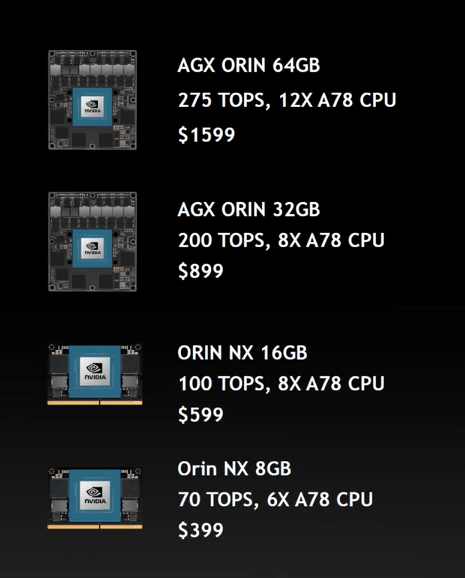
NVIDIA is offering the Orin module in a range of configurations, depending on your computational needs and budget. At the high end is the AGX Orin 64 GB at $1599 USD; which offers a 12-core ARM Cortex-A78AE processor, 32 GB of DDR5 RAM, 64 GB of onboard flash, and a Ampere GPU with 2048 CUDA cores and 64 Tensor cores, which all told enables it to perform an incredible 275 trillion operations per second (TOPS).
At the other end of the spectrum is the Orin NX 8 GB, a SO-DIMM module that delivers 70 TOPS for $399. It’s worth noting that even this low-end flavor of the Orin is capable of more than double the operations per second as 2018’s Jetson AGX Xavier, which until now was the most powerful entry in the product line.
The Jetson AGX Orin Developer Kit is available for $1,999 USD, and includes the AGX Orin 64 GB module. Interestingly, NVIDIA says the onboard software is able to emulate any of of the lower tier modules, so you won’t necessarily have to swap out the internal modules if your final hardware will end up using one of the cheaper modules. Of course the inverse of that is even folks who only planned on using the more budget-friendly units either have to shell out for an expensive dev kit, or try to spin their own breakout board.
While the $50 USD Jetson Nano is far more likely to be on the workbench of the average Hackaday reader, we have to admit that the specs of these new Orin modules are very exciting. Then again, we’ve covered several projects that used the previously top-of-the-line Jetson Xavier, so we don’t doubt one of you is already reaching for their wallet to pick up this latest entry into NVIDIA’s line of diminutive powerhouses.


















