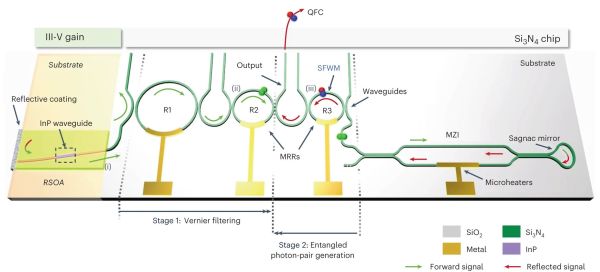
While the few minutes it takes for a spacecraft’s booster rocket to claw its way out of Earth’s gravity well might be the most obviously hazardous period of the mission, an incredible number of things still need to go right before anyone on the ground can truly relax. Space is about as unforgiving an environment as you can imagine, and once your carefully designed vehicle is on its way out to the black, there’s not a whole lot you can do to help it along if things don’t go according to plan.
That’s precisely where the European Space Agency (ESA) currently finds themselves with their Jupiter Icy Moons Explorer (Juice) spacecraft. The April 14th launch from the Guiana Space Centre went off without a hitch, but when the probe’s 16 meter (52 foot) radar antenna was commanded to unfurl, something got jammed up. Judging by the images taken from onboard cameras, the antenna has only extended to roughly 1/3rd its total length.
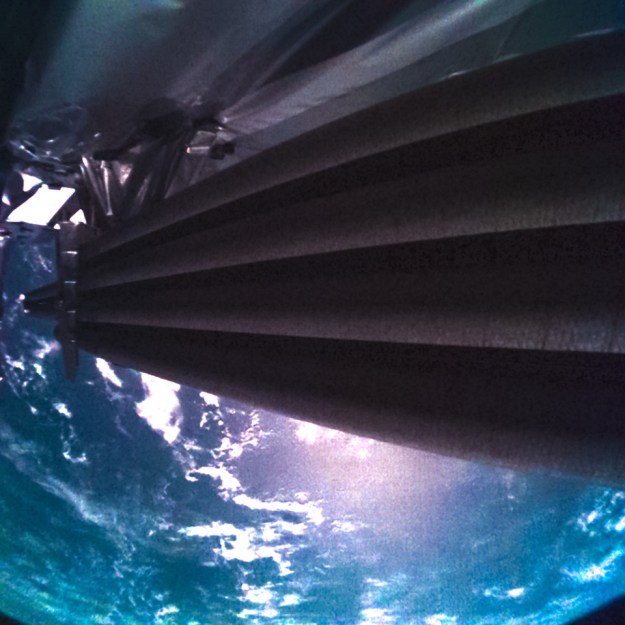
The going theory is that one of the release pins has gotten stuck somewhere, preventing the antenna from moving any further. If that’s the case, it could mean jiggling the pin a few millimeters would get them back in the game. Unfortunately, there’s no gremlins with little hammers stowed away in the craft, so engineers on the ground will have to get a little more creative. Continue reading “ESA’s Jupiter-bound Probe Hits Antenna Snag”