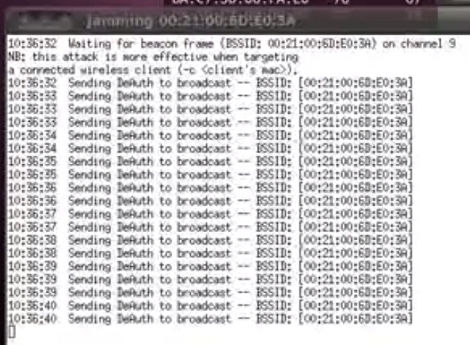
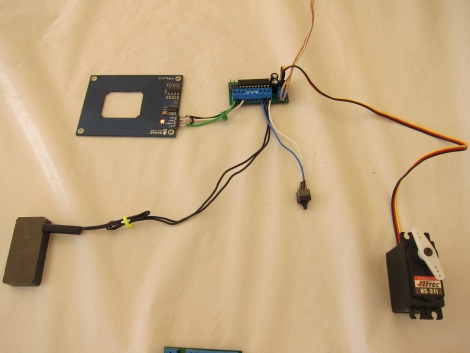
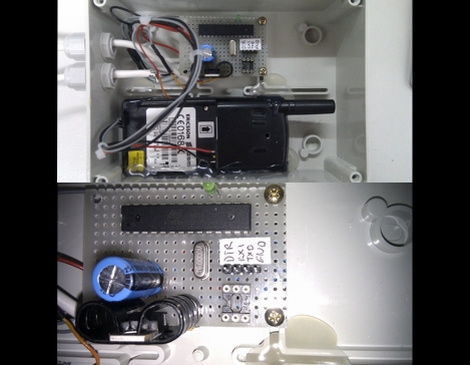
It’s been a while since we checked in on [Travis Goodspeed]. His latest post makes RF sniffing with the Next HOPE badge more portable by ditching the need to display data on a computer. He’s built on the work he did at the beginning of the year, replacing the FTDI chip on the badge with a Bluetooth module. Now he can use his Nokia N900 as a GoodFET terminal to not only display the packets pulled from the air, but the control the badge as well.
Previously, the client running on the computer was communicating with the badge via a serial connection. To get it working on the N900 [Travis] transitioned from using py-serial over to using py-bluez. All of the code changes are available from the GoodFET repository.
He’s got a few other tricks planned for this concept. He put in a parts order to add Bluetooth to the Girltech IM-ME. The pretty pink pager has the same radio chip on board, so adding Bluetooth connectivity will allow it to be used in the same way. There are also plans in the works to add a couple other packet sniffing protocols to the bag of tricks, including ZigBee.