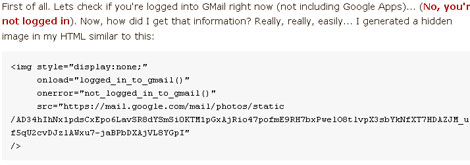
Concerns over privacy online are an ever growing theme. Every day we see people complaining about the policies of facebook and the like. [Mike Cardwell] points out another method of gleaning a bit of personal data from you that you may not have seen yet. By embedding a hidden image or using some really simple javascript, he can tell if you are currently logged into Gmail, Twitter, Facebook, or Digg. While this could possibly be used for more nefarious things, he points out that you could also use it for customizing your website to better suit the experience of the browser. For example, if the “reader” is already logged into Gmail, you could have any email links automatically open a gmail instance instead of the local mail client.