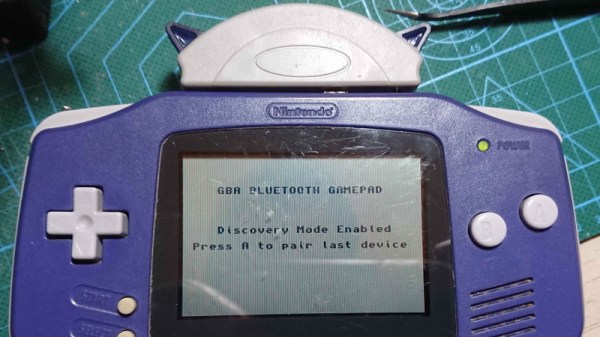
Last year we brought word of a project from [Shyri Villar] that turned a stock Game Boy Advance into a Bluetooth controller by exploiting the system’s “multiboot” capability. The prototype hardware was a bit ungainly, but the concept was certainly promising. We’re now happy to report that the code has been ported over to the ESP32, making the project far more approachable.
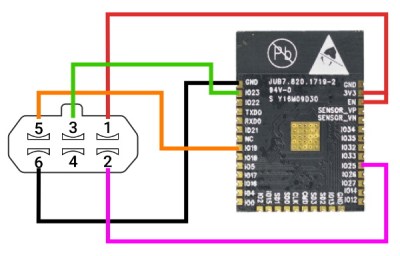 To clarify, the ESP32 is now the only component required for those who want to play along at home. Just five wires connect the microcontroller to the GBA’s Link Cable connector, which is enough to transfer a small ROM over to the system and ferry user input to the Bluetooth hardware. Even if you aren’t interested in using it as a game controller, this project is an excellent example of how you can get your own code running on a completely stock GBA.
To clarify, the ESP32 is now the only component required for those who want to play along at home. Just five wires connect the microcontroller to the GBA’s Link Cable connector, which is enough to transfer a small ROM over to the system and ferry user input to the Bluetooth hardware. Even if you aren’t interested in using it as a game controller, this project is an excellent example of how you can get your own code running on a completely stock GBA.
While the original version of the hardware was a scrap of perfboard dangling from the handheld’s expansion connector, reducing the part count to one meant [Shyri] was able to pack everything into a tidy enclosure. Specifically, a third party GBA to GameCube link cable. This not only provides a sleek case for the microcontroller that locks onto the handheld with spring loaded tabs, but also includes a male Link Cable connector you can salvage. It looks as though there’s a bit of plastic trimming involved to get the ESP32 to fit, but otherwise its a very clean installation.
The GBA will be 20 years old soon, but that doesn’t mean the hardware and software exploration is over. The original Game Boy is over 30, and people are still giving talks about it.