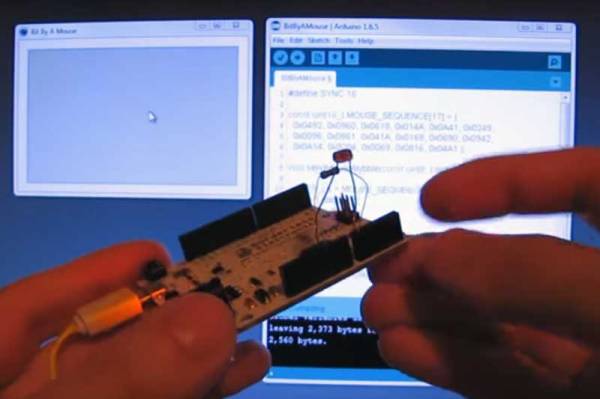
While schools have been using robots to educate students in the art of science and engineering for decades now, not every school or teacher can afford to put one of these robots in the hands of their students. For that reason, it’s important to not only improve the robots themselves, but to help drive the costs down to make them more accessible. The CodiBot does this well, and comes in with a price tag well under $100.
The robot itself comes pre-assembled, and while it might seem like students would miss out on actually building the robot, the goal of the robot is to teach coding skills primarily. Some things do need to be connected though, such as the Arduino and other wires, but from there its easy to program the robot to do any number of tasks such as obstacle avoidance and maze navigation. The robot can be programmed using drag-and-drop block programming (similar to Scratch) but can also be programmed the same way any other Arduino can be.
With such a high feature count and low price tag, this might be the key to getting more students exposed to programming in a more exciting and accessible way than is currently available. Of course, if you have a little bit more cash lying around your school, there are some other options available to you as well.







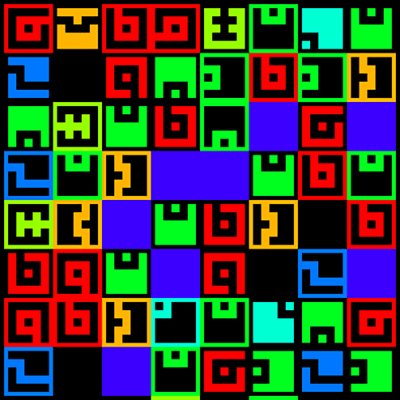 The hackaday illuminati included one additional piece of information with their encoded static image: a 12×12 pixel bitmap. When this bitmap was XORed with the main image, symbols appeared. In total, there are only seven unique symbols in the image. These symbols seem to be stolen from the
The hackaday illuminati included one additional piece of information with their encoded static image: a 12×12 pixel bitmap. When this bitmap was XORed with the main image, symbols appeared. In total, there are only seven unique symbols in the image. These symbols seem to be stolen from the