Whether you’re at the hobbyist level or a professional, if you’re working on code for operating systems or file systems, tools can make or break the job. [Ben Lunt] is an enthusiast hacker himself, and found that over time, a series of useful utilities had proliferated beyond reasonable management. It was time to solve the problem – enter ULTIMATE.
ULTIMATE is a combination of a wide swathe of file system hacking tools that [Ben] had developed over the preceding years. Capable of dealing with most FAT variants, Ext4, ISO, [Ben]’s own FYS FS as well as other Linux ephemera, it enables a wide variety of common tasks to be executed from within a single program.
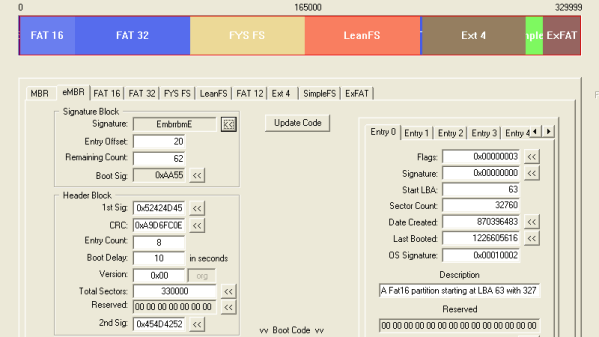
Capabilities of the tool are wide ranging. Files can be inserted into and removed from image files, boot records can be altered, and there’s even the ability to tinker with GPTs for UEFI-based systems. [Ben] has also experimented with the concept of the eMBR – an extended Master Boot Record with greater functionality for larger, modern hard drives.
ULTIMATE is a testament to [Ben]’s broad file system knowledge, and could likely serve useful to many hackers in the file system and OS community. Just be cautious, though – the software is still in an early stage of development. If you’re just getting started in this particular realm of tinkering, take our primer on file system forensics.