We just closed out the Internet of Useful Things round of the Hackaday Prize, which means we’re neck deep in judging projects to move onto the final round this fall. Last week, everyone on Hackaday.io was busy getting their four project logs and illustrations ready for the last call in this round of the Hackaday Prize. These projects are the best of what the Internet of Things has to offer because this is the Internet of Useful things.
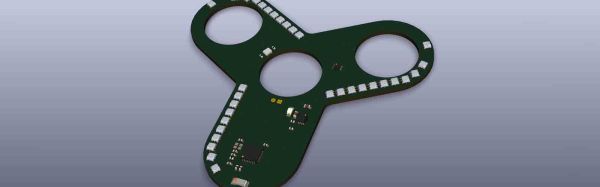
We’re not sure how [Matthias]’ project will rank. It’s an Internet of Things fidget spinner. Yeah, we know, but there are some interesting engineering challenges in building an Internet-connected fidget spinner.
This is a PoV fidget spinner, which means the leading edges of this tricorn spinner are bedazzled with APA102 LEDs. Persistence-of-vision toys are as old as Hackaday, and the entire idea of a fidget spinner is to spin, so this at least makes sense.
These PoV LEDs are driven by an ESP8285, or an ESP8266 with onboard Flash. This is probably the smallest wireless microcontroller you can find, an important consideration for such a small build. Power comes from a tiny LiPo, and additional peripherals include an accelerometer to measure wobble and an optical switch to measure the rotation speed.
These electronics are fairly standard, and wouldn’t look out of place in any other project in The Hackaday Prize. The trick here is mechanical. [Matthias] needs to mount a skateboard bearing to a PCB, and no one has any idea how he’s going to do that. A fidget spinner should be well-balanced, and again [Matthias] is running into a problem. Has anyone here ever done mass and density calculations on PCBs and lithium cells? Is it possible to 3D print conformal counterweights? Has science gone too far?
Will the Internet of Things PoV Fidget Spinner make it to the finals round of The Hackaday Prize? We’ll need to wait a week or so to find out. One thing is for certain, though: you’re going to see this on AliBaba before September.