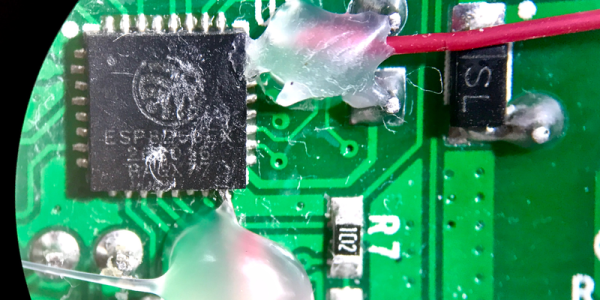
With a plethora of IoT projects and inexpensive commercial smart light fittings and mains switches appearing, you might be forgiven for thinking that another offering in this crowded marketplace would be superfluous. But there is always room for improvement in any field, and in this particular one [Xose Pérez] has done just that with his Espurna board.
This board is a very well executed ESP8266 mains relay, with an on-board mains power supply and power monitoring. It was designed with his Espurna (“Spark” in Catalan) custom firmware in mind, which offers support for Alexa, Domoticz, Home Assistant and anything that supports MQTT or HTTP REST APIs.
Best of all, it’s a piece of open source hardware, so you can download everything you need from his GitHub repository to create your own. For the ultimate in convenience you can even order the PCB ready-made from OSH Park.
As a demonstration of the Espurna board in a real application, he’s produced a smart socket project neatly enclosed in a wall-wart style box with an inbuilt Euro style plug and socket.
We’ve featured [Xose]’s work several times before here at Hackaday, he’s something of an IoT wizard. Most recently there was his work with Alexa and the ESP8266, but before that was his MQTT LED array for his laundry monitor.