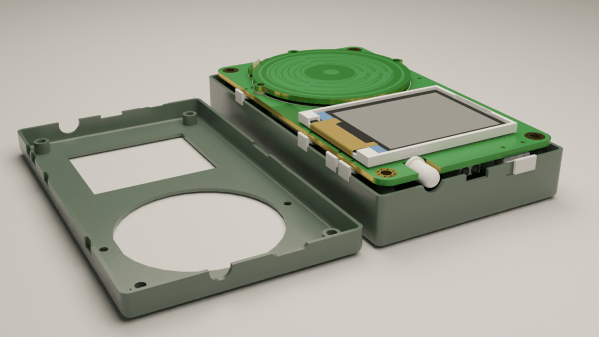
These days, the personal MP3 player has been largely replaced by the the smartphone. However, [Justinas Petkauskas] still appreciates the iPod for its tactility and portability, and wanted to bring that vibe back. Enter JPL.mp3
The build is based around the ESP32-S3 microcontroller. It’s hooked up with a PCM5102 DAC hooked up over I2S to provide quality audio, along with a micro SD card interface for music storage, and a small IPS LCD. The best feature, though? The mechanical click-wheel which provides a very tactile way to scroll and interact with the user interface. Everything is assembled into a neat 3D printed case, with a custom four-layer PCB lacing all the electronics together.
On the software side, [Justinas] cooked up some custom software for organizing music on the device using a SQLite database. As he primarily listens to classical music, the software features fields for composer/piece and conductor, orchestra, or performer.
[Justinas] calls the final build “chunky, but nevertheless functional” and notes it is “vaguely reminiscent of classic iPods.” We can definitely see the fun in building your own personalized version of a much-enjoyed commercial product, for sure. Meanwhile, if you’re cooking up your own similar hardware, we’d certainly love to hear about it.