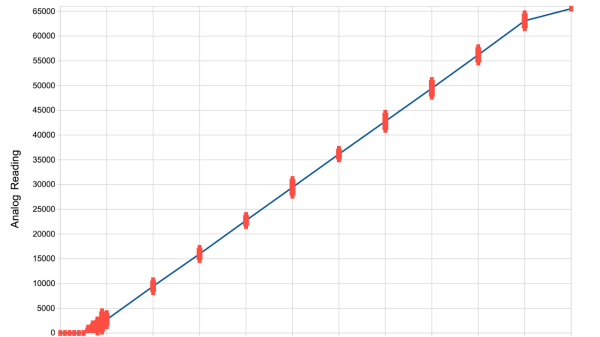
[Simon Monk] got frustrated with bad ADC performance when tinkering with an ESP32 board, and decided to put three of the nowadays-iconic boards to the test – a classic ESP32 devboard, a Pi Pico with an RP2040, and an Arduino Uno R3 with an ATmega328P. To do that, he took a bench PSU, added a filter circuit to it, went through the entire ADC range for each board, took a large number of samples at different points and plotted the results. The plots show us both linearity and precision, as well as ADC dead zones, and the results are quite surprising.
The ESP32 doesn’t only have the most limited ADC with maximum 1V input, it also produces the worst results out of all three, with large error bars and sizeable dead zones at both ends. The Pi Pico, despite being colloquially known for its subpar ADC, produces better results than the ESP32. However, both of them are dwarfed by the ATMega328P’s performance. If you need a dedicated ADC, it might just be a good idea to put an ATMega328P on your board.
The example code is provided, and we are wondering whether there are methodology errors. For instance, the ATMega328P code is written in Arduino-supplied C++, but ESP32 and RP2040 in particular used MicroPython, which does more than just running the code, and MicroPython for ESP32 in particular creates a WiFi access point – something known to induce noise into ADC readings. Nevertheless, this is a fun comparison, and we like when hackers do microcontroller standoffs like that – for instance, check out this review from 2017 which pits a dozen microcontrollers of the time against each other!