OK, that headline is a bit of a cheap shot. But if you run the curl binary that Apple ships, you’re in for a surprise if you happen to use the --cacert flag. That flag specifies that TLS verification is only to be done using the certificate file specified. That’s useful to solve certificate mysteries, or to make absolutely sure that you’re connecting to the server you expect.
What’s weird here is that on a MacOS, using the Apple provided curl binary, --cacert doesn’t limit the program to the single certificate file. On an Apple system, the verification falls back to the system’s certificate store. This is an intentional choice by Apple, but not one that’s aimed particularly at curl. The real magic is in Apple’s SSL library, which forces the use of the system keychain.
The current state of things is that this option is simply not going to do the right thing in the Apple provided binary. It’s documented with the note that “this option is supported for backward compatibility with other SSL engines, but it should not be set.” It’s an unfortunate situation, and we’re hopeful that a workaround can be found to restore the documented function of this option. Continue reading “This Week In Security: Apple Backdoors Curl, Tor’s New Bridge, And GhostRace”




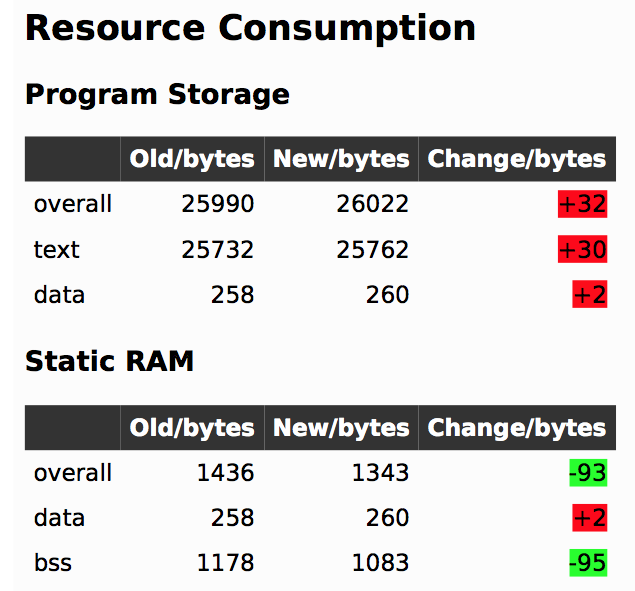 In firmware-land, where flash space can be limited, it’s nice to keep a handle on code size. This can be done a number of ways. Manual inspection of .map files (colloquially “mapfiles”) is the easiest place to start but not conducive to automatic tracking over time. Mapfiles are generated by the linker and track the compiled sizes of object files generated during build, as well as the flash and RAM layouts of the final output files.
In firmware-land, where flash space can be limited, it’s nice to keep a handle on code size. This can be done a number of ways. Manual inspection of .map files (colloquially “mapfiles”) is the easiest place to start but not conducive to automatic tracking over time. Mapfiles are generated by the linker and track the compiled sizes of object files generated during build, as well as the flash and RAM layouts of the final output files.