It does sound a bit silly — the idea that given enough time, a plant could influence the order of hardware-generated random numbers in order to get enough light to survive. But not so silly that [DeckerM] couldn’t wait to try it out after seeing a short clip about an unpublished study done at Princeton’s Engineering Anomalies Research (PEAR) lab that came to this very conclusion. The actual verbatim conclusion from the clip: “It’s as though life itself – even life or consciousness in something as simple as a house plant, bends probability in the physical world in the direction of what it needs, in the direction of its growth and evolution.”
 The idea is this: a plant is made to suffer by languishing in the corner of a windowless room. The room has exactly one light in the middle of the ceiling — a repositionable spotlight of sorts that can only shine into any of the four corners and is controlled by a random number generator. A set of dividers ensure that none of the light leaks out of the quadrant and into any of the others.
The idea is this: a plant is made to suffer by languishing in the corner of a windowless room. The room has exactly one light in the middle of the ceiling — a repositionable spotlight of sorts that can only shine into any of the four corners and is controlled by a random number generator. A set of dividers ensure that none of the light leaks out of the quadrant and into any of the others.
[DeckerM]’s recreation of this experiment is much more practical. It’s essentially a little plywood cabinet with four open partitions and a ceiling. Each quadrant has a grow light strip planted in the corner, and all the wires are run through the top, where each has been stripped of its pesky power-governing controller and rewired to go straight into a smart plug. [DeckerM] is using a hardware RNG hosted on a Raspberry Pi, which is running a Python script that takes numbers from the RNG that corresponds to one of the quadrants, and then lights that quadrant.
And the results? They don’t really support the PEAR study’s bold conclusion unless viewed in small sample sizes, but [DeckerM] isn’t giving up that easily. Since the paper is unpublished, there are a lot of unanswered questions and juicy variables to play with, like the type, number, and age of the plants used. We’re excited to see if [DeckerM] can shed some light on plant psychokinesis.
Interested in portable plant propagation? A sunny location is usually ideal, but this all-in-one solution can take care of the rest.



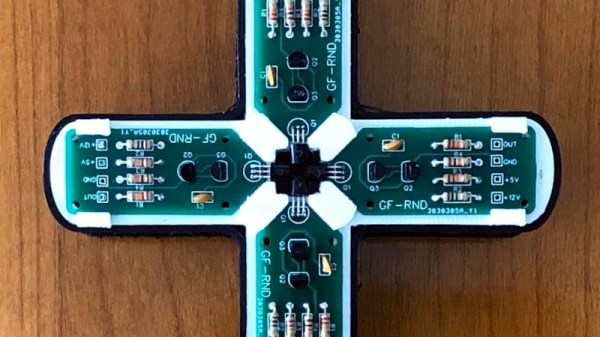
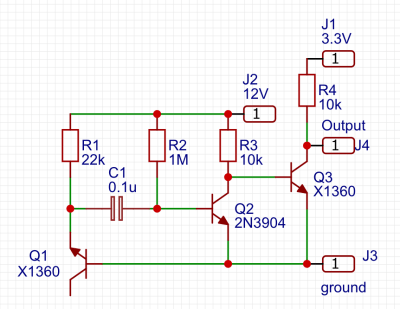 One of the simplest circuits for generating random analogue noise involves a reverse biased diode in either Zener or avalanche breakdown, and it is a variation on this that he’s using. A reverse biased emitter junction of a transistor produces noise which is amplified by another transistor and then converted to a digital on-off stream of ones and zeroes by a third. Instead of a shift register to create his four bits he’s using four identical circuits, with no clock their outputs randomly change state at will.
One of the simplest circuits for generating random analogue noise involves a reverse biased diode in either Zener or avalanche breakdown, and it is a variation on this that he’s using. A reverse biased emitter junction of a transistor produces noise which is amplified by another transistor and then converted to a digital on-off stream of ones and zeroes by a third. Instead of a shift register to create his four bits he’s using four identical circuits, with no clock their outputs randomly change state at will.