If you are writing a program that has a technical user base, it is a nice touch to make the program scriptable. In fact, you might want to do the hard work in a programming language and then use your scripting language to build out features. In theory, this should be easy. There are plenty of embedded scripting libraries and they provide some way for your code to access script resources and for script resources to access selected host variables and functions. If you use C++, one of the easier ways to do this is with ChaiScript.
ChaiScript is BSD licensed and — assuming your compiler supports C++ 14 — it is as easy as including a header file and making a few calls. There are no special tools or libraries required. The code is portable between operating systems, including both 32-bit and 64-bit Windows. It is also threadsafe unless you turn that feature off.
Continue reading “Add Scripting To Your C++ Programs With ChaiScript”



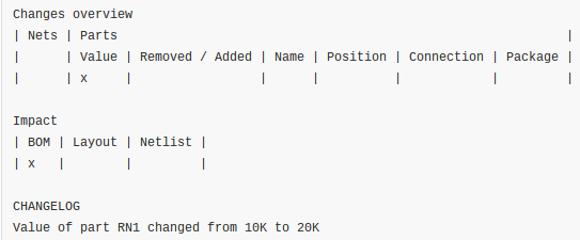 We love Git. We know everyone has their favorite version tracking tools. But even those that don’t care for Git should see the value of
We love Git. We know everyone has their favorite version tracking tools. But even those that don’t care for Git should see the value of