The only thing more surprising than finding out TiVo actually put out a new 4K set-top box recently is learning that somehow they didn’t bother to build WiFi into the thing. You’re forced to buy a special wireless adapter to the tune of $60 USD to add the feature. We’d make a joke about the company living in the past, but frankly, it would be too easy.
Having to buy just one of these expensive dongles in 2020 would be insulting enough, but TiVo superfan [xxbiohazrdxx] needed four of them. Rather than hand nearly $250 to the antennae-headed overlords, they decided to reverse engineer the adapter and produce their own low-cost version. While the final result might not be as slim and svelte as the original, it does come in at less than 1/4 the price.
Operating under the assumption that the TiVo would only talk to a WiFi adapter based on the same Broadcom BCM43569 chipset used in the official one, [xxbiohazrdxx] started by trying to find a standard USB dongle that might be a drop-in replacement. Unfortunately, it looks like this particular chip was almost exclusively used in proprietary applications, most commonly as a WiFi board inside of smart TVs. But as it turns out, that wasn’t necessarily a deal breaker.
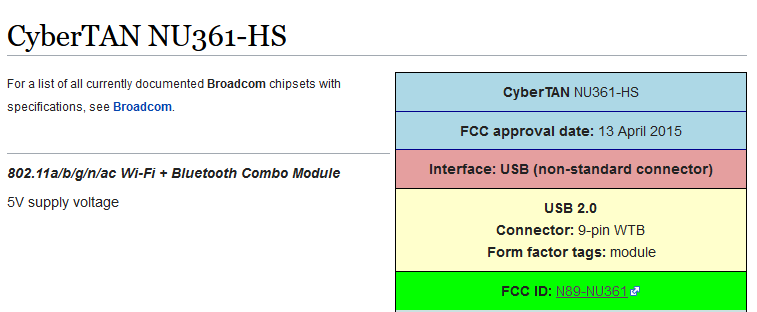 After some searching, [xxbiohazrdxx] eventually found the promising CyberTAN NU361-HS board. Not only was it based on the right chipset and ran from 5 volts, but its FCC ID entry had a complete pinout for the connector. This particular WiFi module is used in a number of budget TVs and is widely available as a spare part for less than $10. By combing the board and a USB breakout PCB inside of a 3D printed case, you’ve got a plug-and-play WiFi adapter that the TiVo thinks is the real deal.
After some searching, [xxbiohazrdxx] eventually found the promising CyberTAN NU361-HS board. Not only was it based on the right chipset and ran from 5 volts, but its FCC ID entry had a complete pinout for the connector. This particular WiFi module is used in a number of budget TVs and is widely available as a spare part for less than $10. By combing the board and a USB breakout PCB inside of a 3D printed case, you’ve got a plug-and-play WiFi adapter that the TiVo thinks is the real deal.
There was a time when Hackaday was flooded with TiVo hacks, but it’s now been more than a decade since cheap carrier-provided DVRs ate the company’s lunch. Realistically, there’s an excellent chance that this post will be the only time a mention of the once-mighty DVR graces the front page in 2020. While the reign of the TiVo might be at its end, the impact it had as one of the first Linux-powered consumer devices will be etched in hacker history forever.