Over the past decade or so, smartphones have exploded in popularity and seamlessly integrated themselves into nearly every aspect of most people’s lives. Although that comes with a few downsides as well, with plenty of people feeling that the smart phone makes it a little too easy to waste time and looking to switch to something simpler, like an older-style flip phone. If this style of phone is more your speed, take a look at this DIY cell phone which takes care of everything a phone really needs to do. (Google Translate from French)
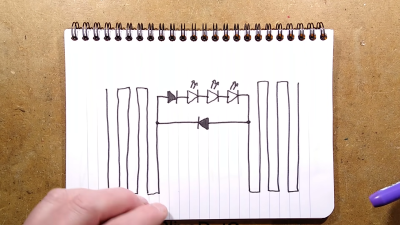
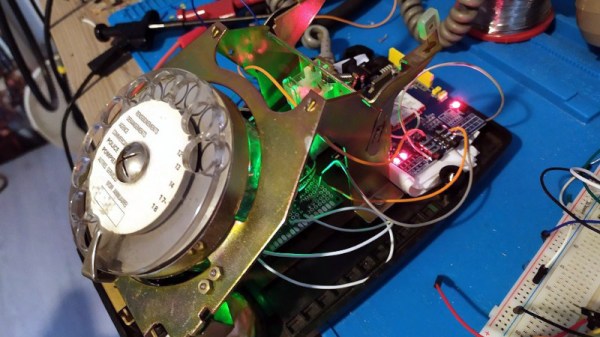
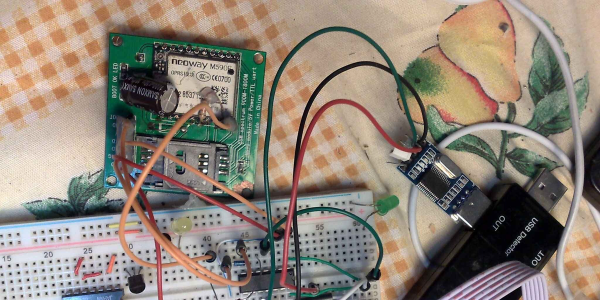
The phone uses an ESP32 at its core, with a SIM800L GSM modem to interact with the cell network, including retrieving the system time. A small battery is included as well as all of the support circuitry for charging it as well as a USB interface that can communicate to a PC. The operating system for the phone is built from the ground up as well, with a touch screen interface allowing the user to make phone calls, send text messages, store contacts, and a few other basic features. There’s also a GPS application though, allowing the phone to know basic location information.
Another perk of this device is that its creator, [Gabriel], made the design schematics, print files for the case, and the operating system software completely open source for anyone to build this phone on their own. Everything is available on the project’s GitHub page. It’s a fairly remarkable achievement, especially considering [Gabriel] is only 16. And, if you’re not one to eschew modern smart phone technology there are some DIY smart phones available to build as well.
Thanks to [come2] for the tip!