While networking was once all about the Cat 5 cables and hubs and routers, now most of us connect regularly in a wireless manner. Just like regular networks, wireless networks need auditing, and [Brains933] decided to whip up a tool for just that, nicknaming it the PumpkinPI_3.
The build is inspired by the WiFi Pineapple, which is a popular commercial pentesting tool. It runs the WiFi Pumpkin framework which allows the user to run a variety of attacks on a given wireless network. Among other features, it can act as a rogue access point, run man-in-the-middle attacks, and even spoof Windows updates if so desired.
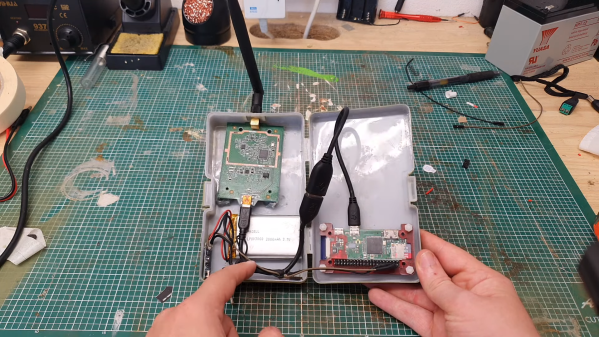
In this case, [Brains933] grabbed a Raspberry Pi Zero W to run the framework. It was stuffed in a case with a Alfa Network AWUS036NHA wireless card due to its ability to run in monitoring mode — a capability required by some of the more advanced tools. It runs on a rechargeable LiPo battery for portability, and can be fitted with a small screen for ease of operation.
It should prove to be a useful tool for investigating wireless security on the go. Alternatively, you can go even leaner, running attacks off an ESP32.
Continue reading “The WiFi Pumpkin Is The WiFi Pineapple We Have At Home”