 Don’t forget to vote in the newest round of Astronaut or Not. In addition to deciding which projects should be recognized as “Too Cool for Kickstarter”, you will be eligible for the voter lottery.
Don’t forget to vote in the newest round of Astronaut or Not. In addition to deciding which projects should be recognized as “Too Cool for Kickstarter”, you will be eligible for the voter lottery.
What is this voter lottery we speak of? On Friday we’ll draw a random number and see if that hacker profile on Hackaday.io has voted at least once in this round, which started on Monday.
If they voted they’ll received a prize package packed with all kinds of prototyping hardware. This cycle offers several breakout boards, a bunch of programmers and debuggers, as well as a digital multimeter and a bench power supply (full list here). For the hackers who haven’t registered a vote? Nothing!
We’ll be drawing the number from a hotel room in Vegas since we’ll be there for DEFCON. If you’re also attending the conference track us down to show off your own hardware or just to grab some stickers.



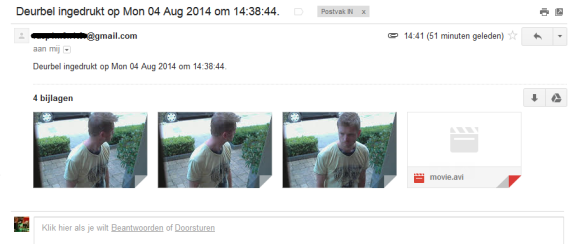
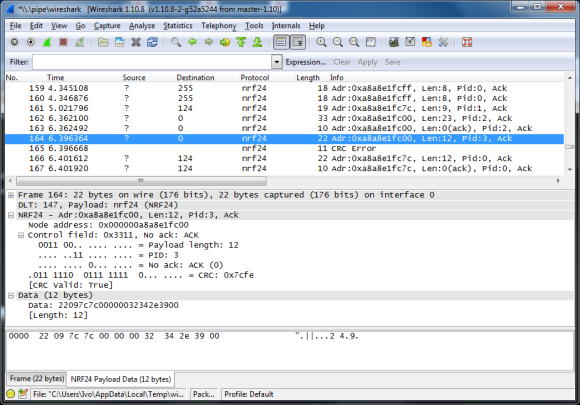
 Last week we published a post about how it was discovered through trial and error that
Last week we published a post about how it was discovered through trial and error that 








