Before the outbreak of coronavirus, the seasonal flu was one of the most dangerous infectious diseases, but a lot of people have trouble telling the difference between a flu and a cold by their symptoms alone. This gave [M. Bindhammer] the idea to design a smart thermometer that can distinguish between flu and cold.
 Automated medical diagnostics is certainly an important technology of the future. [M. Bindhammer]’s project, named F°LUEX, is the second version of his iF°EVE thermometer. After taking the body temperature it asks the patient a set of questions about his symptoms and then calculates the probability of whether it is more likely to be a flu or a cold. [M. Bindhammer] uses a method commonly used in medical diagnostics based on Bayesian statistics which assigns a probability score to both hypotheses. It takes into account how often a certain symptom occurs when you have a common cold or flu as well as the overall probability of catching one or the other.
Automated medical diagnostics is certainly an important technology of the future. [M. Bindhammer]’s project, named F°LUEX, is the second version of his iF°EVE thermometer. After taking the body temperature it asks the patient a set of questions about his symptoms and then calculates the probability of whether it is more likely to be a flu or a cold. [M. Bindhammer] uses a method commonly used in medical diagnostics based on Bayesian statistics which assigns a probability score to both hypotheses. It takes into account how often a certain symptom occurs when you have a common cold or flu as well as the overall probability of catching one or the other.
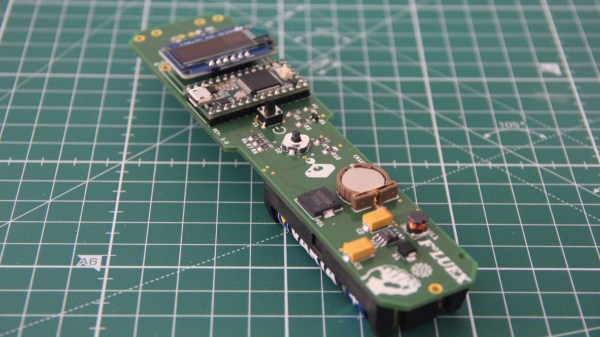
The hardware of the project is based on a custom PCB that includes a medical-grade MLX90614 infrared thermometer with an accuracy of ±0.2˚C around the human body temperature. The sensor is being read out by a Teensy 3.2 and information is displayed on a small OLED screen. Everything is housed in a 3D printed enclosure that received a nice finishing by painting with primer and acrylic spray paint. Unfortunately, [M. Bindhammer] project also got delayed by the corona crisis as his order for the temperature sensor got canceled due to the current high demand. But that does make us wonder how useful this could be to discriminate between cold, flu, and COVID-19.
An IR thermometer is something useful to have around not only for medical applications and can also be built without a custom PCB and minimal parts.