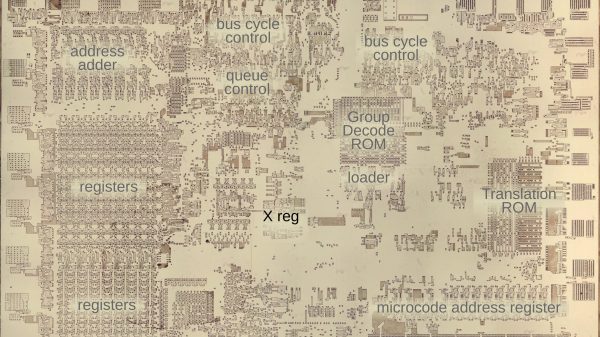
In the United States, analog TV broadcasting officially ended in 2009. While the transition wasn’t without hiccups, we did lose something along the way. For [Emily Velasco], she misses the channels between channels — where an analog TV isn’t quite tuned right and the image is smeared and distorted. A recent bug in one of her projects led to her trying to recreate the experience of the in-between on a CRT.
One of [Emily]’s other projects involved generating composite video signals from an ESP32 microcontroller. While experimenting with adding color to the output signal, the image came out incredibly scrambled. She had made an error in the stride, which smeared the image across the screen. This immediately brought back memories of old analog TV sets. A quick potentiometer allowed her to control the stride error and she wrote some code to break the GIF up into discrete bitmaps for display since the GFX library handles GIFs differently than static images. Next up was vertical hold, which was accomplished by shifting the Y coordinates. With some help from [Roger], there was now a handy GIF library that would draw GIFs line by line with the composite video effects.
She used a Goldbeam portable CRT, soldered the tuning potentiometer to the ESP32, and set up 10 different GIFs to act as “channels” with space in between. It’s a fun and quirky idea, which is exactly the sort of thing [Emily] has been encouraging people to do.
Continue reading “Creating GIFs For The Channels Between Channels”