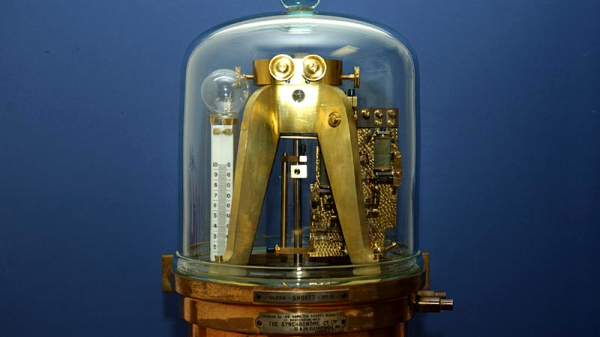
Would you believe a pendulum clock that can keep time accurately to within one second per year? If you answered “yes”, you’ve either never tried to regulate a pendulum clock yourself, or you already know about the Shortt Clock. Getting an electromechanical device to behave so well, ticking accurately to within 0.03 parts per million, is no mean feat, and the Shortt clock was the first timekeeping device that actually behaves more regularly than the Earth itself. Continue reading “Retrotechtacular: The Best Pendulum Clock”
Author: Elliot Williams1450 Articles
Annoy Your Neighbors With MIDI Musical Siren
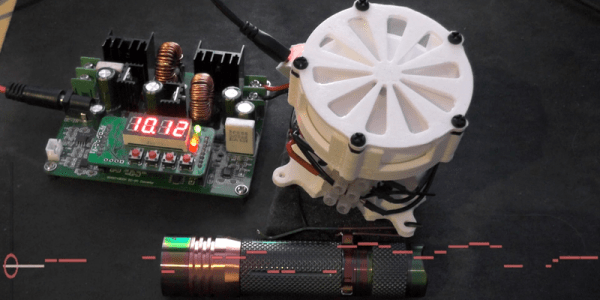
[Yannick], aka [Gigawipf] brings us this (mostly) musical delicacy: a 3D-printed siren that’s driven by a brushless quadcopter motor, and capable of playing (mostly) any music that you’ve got the MIDI score for. This is a fantastic quickie project for any of you out there with a busted quad, or even some spare parts, and a 3D printer. Despite the apparent level of difficulty, this would actually be a great quickie weekend build.
Continue reading “Annoy Your Neighbors With MIDI Musical Siren”
Japanese ISS Supply Ship Dual-Purposed As Tether Experiment
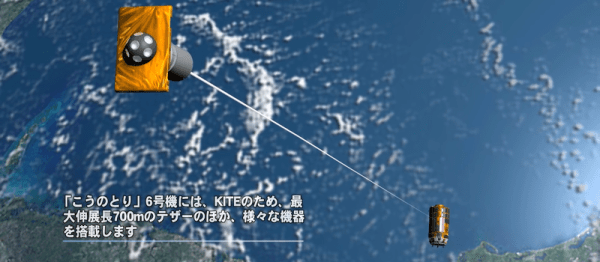
When a rocket sends a capsule up with supplies for the International Space Station, they usually send a bunch of their trash back down with it, all of which burns up in the atmosphere on re-entry. But as long as you’ve got that (doomed) vehicle up there, you might as well do some science with it along the way. And that’s exactly what the Japanese Space Agency (JAXA) is doing with their Kounotori 6 supply ship that just left the ISS on Friday.
The experiment is with an electromagnetic tether that can be used to either turn electrical energy into kinetic or vice-versa. When you string a long conducting wire outwards from earth, the two ends pass through the earth’s magnetic field at different altitudes and thus pass through magnetic fields with different strengths, and an electrical potential is generated. In the KITE experiment (translated), a resistive load and an electron emitter on the supply ship are designed to burn up this electrical energy, lowering the ship’s kinetic energy, and dropping its orbit down to earth.
Continue reading “Japanese ISS Supply Ship Dual-Purposed As Tether Experiment”
Forth: The Hacker’s Language
Let’s start right off with a controversial claim: Forth is the hacker’s programming language. Coding in Forth is a little bit like writing assembly language, interactively, for a strange CPU architecture that doesn’t exist. Forth is a virtual machine, an interpreted command-line, and a compiler all in one. And all of this is simple enough that it’s easily capable of running in a few kilobytes of memory. When your Forth code is right, it reads just like a natural-language sentence but getting there involves a bit of puzzle solving.
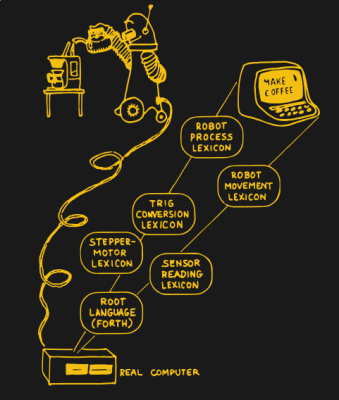
Forth is what you’d get if Python slept with Assembly Language: interactive, expressive, and without syntactical baggage, but still very close to the metal. Is it a high-level language or a low-level language? Yes! Or rather, it’s the shortest path from one to the other. You can, and must, peek and poke directly into memory in Forth, but you can also build up a body of higher-level code fast enough that you won’t mind. In my opinion, this combination of live coding and proximity to the hardware makes Forth great for exploring new microcontrollers or working them into your projects. It’s a fun language to write a hardware abstraction layer in. Continue reading “Forth: The Hacker’s Language”
A Heart For His Girlfriend
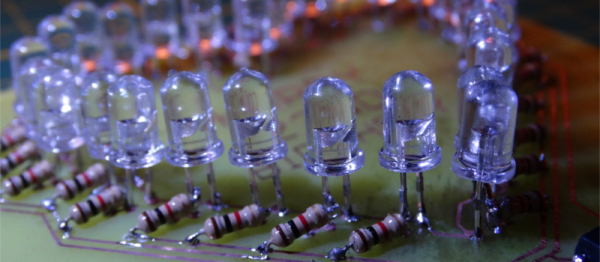
[Decino] made a nice LED animated blinking heart box for his girlfriend. That’s a nice gesture, but more to the point here, it’s a nice entrée into the world of custom hardware. The project isn’t anything more than a home-etched PCB, a custom 3D-printed case, a mess of LEDs and current-limiting resistors, a shift register, and a microcontroller. (OK, we’re admittedly forgetting the Fifth Element.) The board is even single-sided with pretty wide traces. In short, it’s a great first project that ties together all of the basics without any parts left over. Oh, and did we mention Valentine’s day?
Once you’ve got these basics down, though, the world is your oyster. Building almost anything you need is just a matter of refining the process and practice. And if you’ve never played around with shift registers, a mega-blinker project like this is a great way to learn hands-on.
Not everything we write up on Hackaday has to be neural nets and JTAG ports. Sometimes a good beginner project that hits the fundamentals with no extra fat is just the ticket. What’s your favorite intro project?
Ultrasuede Bench Power Supply Got Style
From the look of it sitting on his bench, you’d never guess that [3nz01]’s power supply was actually a couple of el-cheapo modules from eBay, but now we all know the dirty truth.
Re-using or re-purposing an enclosure can be a great way to get a project done faster and get on to the next one. In [3nz01]’s case (tee-hee!), it was an old clock with a broken and annoying buzzer that needed to go. The clock was a nice piece of wood, but that Plexiglas front panel just wasn’t cutting it. That’s why it’s good to have a tailor for a father — a suitable piece of ultrasuede wrapped around the plexi makes the build look swank.
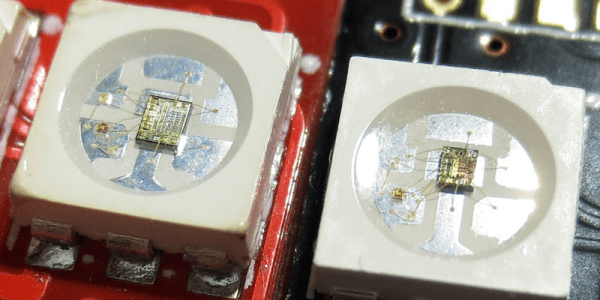
WS2812B LED Clones: Work Better Than Originals!
Commodity electronics manufacturing is a tough game. If you come out with a world-beating product, like WorldSemi did with the WS2812B addressable RGB LED “pixel”, you can be pretty sure that you’re going to be cloned in fairly short order. And we’re all used to horror stories of being sold clones instead of what was ordered. But what if the clones were actually an improvement?
[Gonazar] bought some strips of “WS2812” LEDs and prototyped a project. When stepping up to larger production, he thought he’d go directly to WorldSemi. Long story short, the cheaper LED modules that he’d previously bought weren’t from WorldSemi, but were actually SK6812 clones labelled as WS2812Bs. When he switched to the real thing, he discovered that they had some temperature and pressure sensitivities that the clones didn’t. The clones were better!
They weren’t even straight clones. It turns out that they have a much higher PWM frequency, resulting in less flicker at low brightnesses. The distributor came clean, saying that they swapped them out without note because they spoke the same protocol, but were a strict improvement.
Continue reading “WS2812B LED Clones: Work Better Than Originals!”