If you’re looking for a simple way to make an RF transmitter, check out [Tomasz]’s Morse code transmitter. His design uses nothing more than a microcontroller and a 16MHz crystal to transmit CW Morse code on 96MHz. We’ve seen some similar designs that work at lower frequencies, but transmitting up at 96MHz is pretty impressive.
[Tomasz] used an STM32L microcontroller for this project, which isn’t specced to run up at the high frequencies he wanted to transmit at. To get around this, [Tomasz] wired a 16Mhz oscillator up to microcontroller’s clock input. The clock input is run into the micro’s PLL which is capable of generating high frequencies. He mentions that you can use the internal oscillator instead of a crystal, but it has a ton of phase noise and splatters all over the spectrum.
[Tomasz] chose to start transmitting at 96MHz, which can be picked up by a standard FM radio. To generate this frequency, he set the PLL to multiply the 16MHz crystal up to 192MHz followed by a clock divide of 2 which brings it down to 96MHz. The microcontroller’s CPU runs on the 16MHz crystal input before it goes into the PLL. Next [Tomasz] enabled the MCO clock output pin which routes the 96MHz signal to the outside world.
Transmitting CW is pretty simple; it just involves turning a fixed-frequency transmitter on and off. [Tomasz] wrote a function that enables and disables the MCO output pin. This has the effect of keying any Morse code string you throw at it. Check out the video after the break to see the transmitter in action.
Continue reading “Morse Code RF Transmitter From A Micro’s Clock Output”



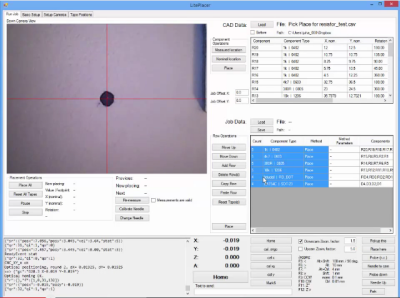 While some other DIY pick and place setups we’ve featured use fairly exotic setups
While some other DIY pick and place setups we’ve featured use fairly exotic setups 

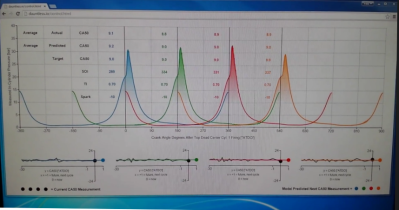 [Adam]’s algorithm calculates engine control parameters in real-time on the Pi based on the pressure readings and crankshaft position. The control values are sent over CAN to the low-level engine controller. The Pi monitors changes in the engine’s performance with the new values, and makes changes to its control values to optimize the combustion cycle as the engine runs. The Pi also serves up a webpage with graphs of the crankshaft position and cylinder pressure that update in real-time to give some user feedback.
[Adam]’s algorithm calculates engine control parameters in real-time on the Pi based on the pressure readings and crankshaft position. The control values are sent over CAN to the low-level engine controller. The Pi monitors changes in the engine’s performance with the new values, and makes changes to its control values to optimize the combustion cycle as the engine runs. The Pi also serves up a webpage with graphs of the crankshaft position and cylinder pressure that update in real-time to give some user feedback.










