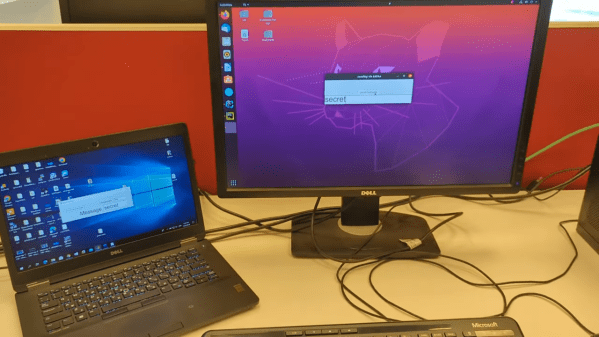
It seems like [Mordechai Guri]’s lab at Ben-Gurion University is the place where air-gapped computers go to die, or at least to give up their secrets. And this hack using a computer’s SATA cable as an antenna to exfiltrate data is another example of just how many side-channel attacks the typical PC makes available.
The exploit, deliciously designated “SATAn,” relies on the fact that the SATA 3.0 interface used in many computers has a bandwidth of 6.0 Gb/s, meaning that manipulating the computer’s IO would make it possible to transmit data from an air-gapped machine at around 6 GHz. It’s a complicated exploit, of course, and involves placing a transmitting program on the target machine using the usual methods, such as phishing or zero-day exploits. Once in place, the transmitting program uses a combination of read and write operations on the SATA disk to generate RF signals that encode the data to be exfiltrated, with the data lines inside the SATA cable acting as antennae.
SATAn is shown in action in the video below. It takes a while to transmit just a few bytes of data, and the range is less than a meter, but that could be enough for the exploit to succeed. The test setup uses an SDR — specifically, an ADALM PLUTO — and a laptop, but you can easily imagine a much smaller package being built for a stealthy walk-by style attack. [Mordechai] also offers a potential countermeasure for SATAn, which basically thrashes the hard drive to generate RF noise to mask any generated signals.
While probably limited in its practical applications, SATAn is an interesting side-channel attack to add to [Dr. Guri]’s list of exploits. From optical exfiltration using security cameras to turning power supplies into speakers, the vulnerabilities just keep piling up.
Continue reading “SATAn Turns Hard Drive Cable Into Antenna To Defeat Air-Gapped Security”