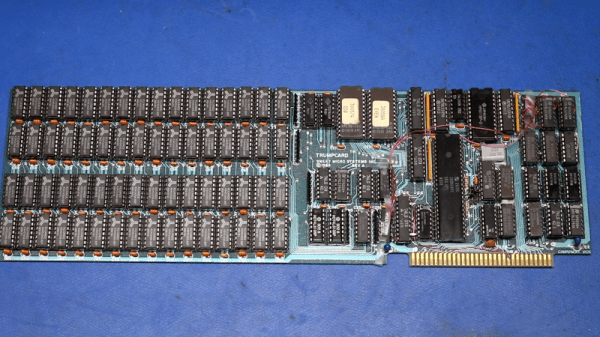
[Smbakeryt] needs your help. He bought a 1984-vintage Z8000 coprocessor card for the PC, but the software is missing in action. Apparently, the co-processor — called a Trump Card — appeared in Byte magazine courtesy of the famous [Steve Ciarcia]. The schematics were published, and if you sent [Steve] proof that you built it, he’d send you the software. The product was later commercialized, but no one seems to have the software, so [Smbakeryt] is on the lookout for it.
The board itself was pretty amazing for its day. It added a 16-bit Zilog Z8000 CPU with 512 K of RAM. Big iron for 1984 and a good bit more performance than a stock IBM PC of the era.
We miss the days when computer gear came with big binders of documentation. These days, you are more likely to get a sticker with a URL. The Z8000 was a nice processor and could emulate the Z80, but it never became hugely popular. In addition to Zilog’s System 8000, the CPU found its way into some Unix computers including the Onyx C8002 and several Olivetti computers. Commodore planned to use the CPU in a canceled project. The Z8000 was famous for not using microcode and, thus, it fit on a relatively small die with 17,500 transistors (compared to the 8086’s 29,000 transistors).
We hope someone can help out with the software. If you want your own Z8000 system, you might be better off with Clover. Or, stick with a Z80 on the cheap.